
This analysis will cover the extraction of Quasar configuration via Dnspy. We'll then use this information to pivot to additional servers utilising Shodan and Censys. In total, 64 additional servers will be identified.
A full list of the 64 Quasar servers can be found at the end of this post.
An overview of this post
- Obtaining the initial sample
- Overview of the unpacking process
- Locating and extracting Quasar configuration using Dnspy
- Analysis of Quasar Configuration
- Building Shodan Queries
- Analysis of identified servers
- Cross-referencing detection rates with VirusTotal
- Identifying additional servers using Censys
- Complete list of identified servers.
Sample
The malware sample was obtained from Malware Bazaar and is available here.
SHA256:78eb982abdfb385ac2e0c9a640856077379355f16e29788456a6551c166b00fe
the
I'll leave the bulk of Quasar unpacking for another post. This is a high-level summary of the process that I used.
- Unzip the file using the password
infected - Identify high-entropy using
detect-it-easy - Check strings and observe multiple references to
ZwWriteVirtualMemoryandInstallUtil.exe - Assume
entropy=Loader, - Assume
InstallUtil.exe = Injection Target - Execute malware inside the Virtual Machine
- Utilise
Process Hackerto observe new spawns ofinstallutil.exe - Use
Process Hackerto observe .NET assemblies loaded intoInstallutil.exe - Utilising
DnSpyto dump .NET assemblies. Obtain Quasar RAT. - Load Quasar into Dnspy. Browse to Entry Point.
- Observe the config initialization function. Set breakpoints and create a watch window.
- Obtain Configuration.
Extracting Configuration From Quasar Rat
Following the steps above will identify the following code. Portions of the code have been renamed for readability.
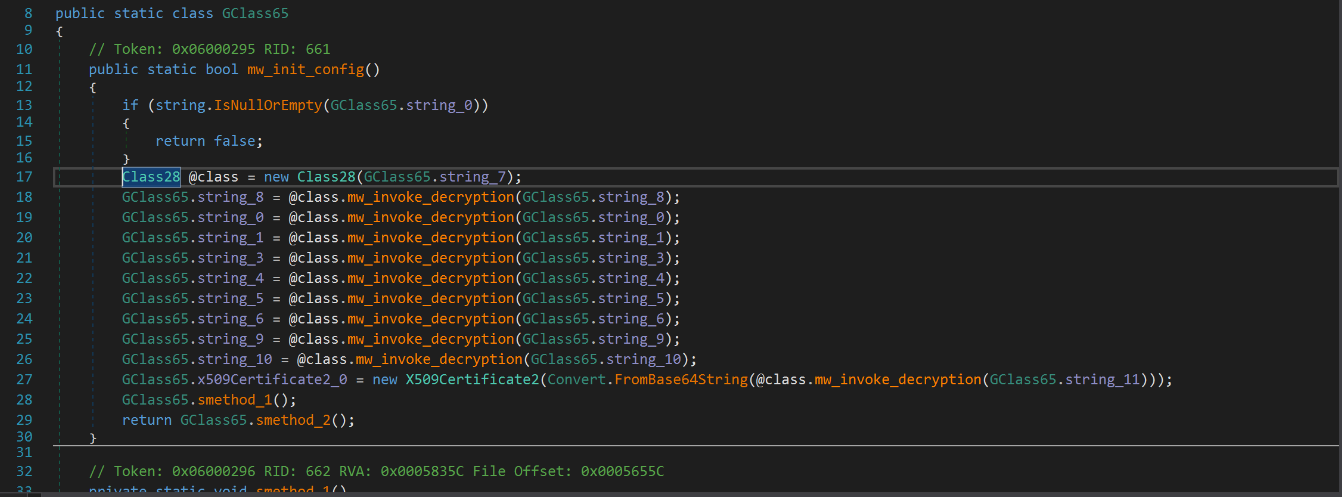
Each of the GClass65.string_8 values reference a value that has been encrypted using AES and then encoded using base64.
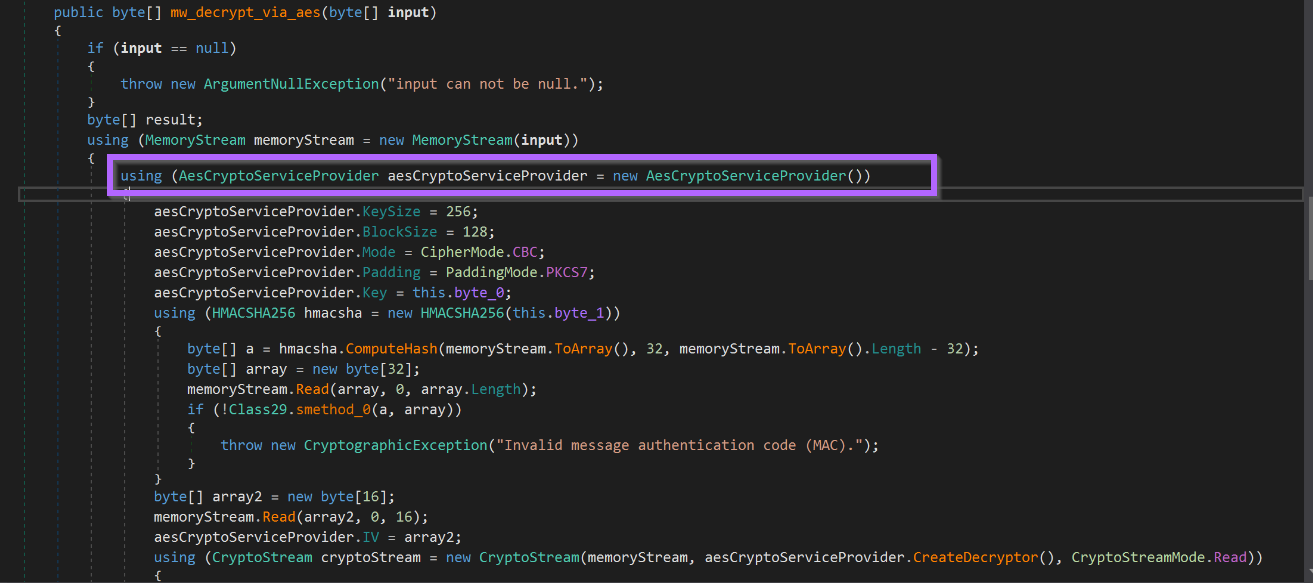
The AES decryption code can be seen below.
As well as a reference to additional base64 encoding, on top of the initial AES encryption.
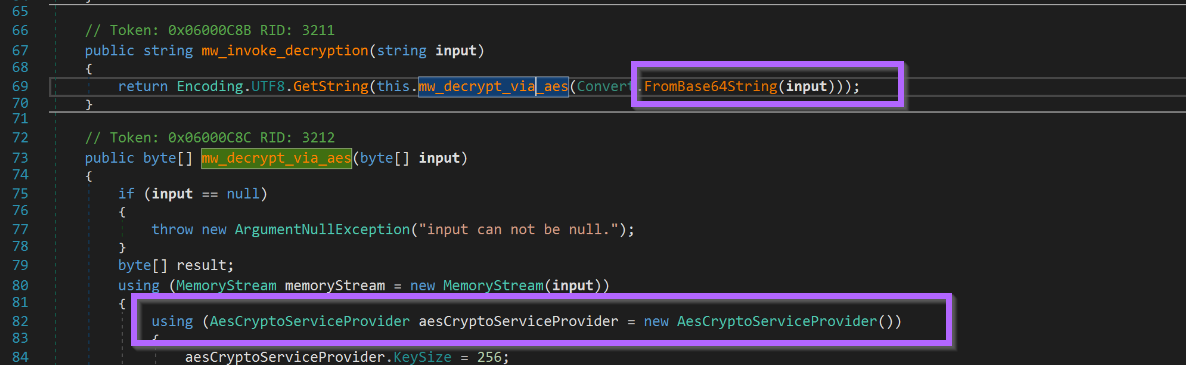
By setting appropriate breakpoints and watch windows. The configuration can be obtained with minimal analysis of the encryption.
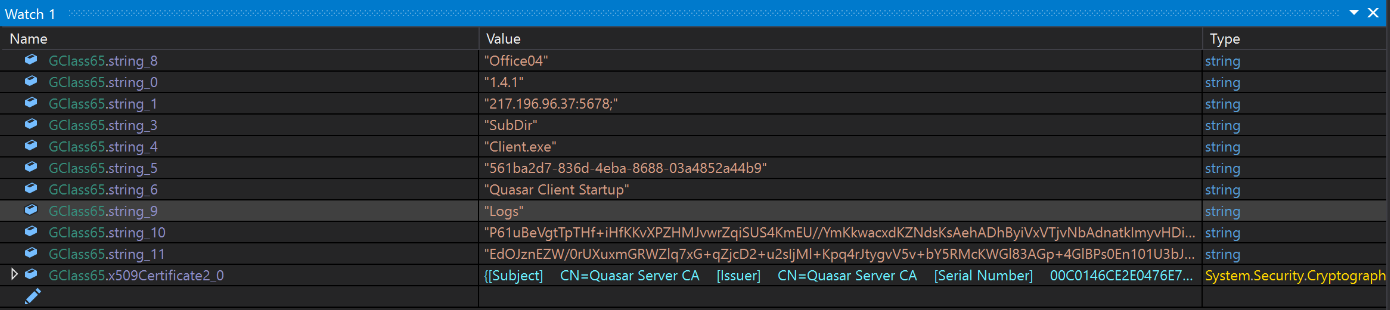
Analysis of the Quasar Configuration
The most interesting components of the configuration are the (likely) c2 of 217.196[.]96.37:5678 , as well as the x509 Certificate used for SSL/TLS communications.
An x509 certificate forms part of the public-key component of TLS communications performed between a client and server. The certificate contains valuable information about who is "endorsing" the communications, and who exactly is being endorsed
There are some detailed writeups with much better explanations from Sectigo and Wikipedia.
Typically I have ignored x509 certificates. But today will be a little bit different.
The x509 certificate contains a subject and issuer value of Quasar Server CA.
Of particular note is that the x509 certificate was initially encrypted by the malware. This is an indication that it contains something valuable that could hinder the malware if revealed and appropriately analysed.
Generally, I would stop my analysis here as the C2 was successfully found.
Today I will take this one step further, based on some infrastructure-hunting posts from @MichalKoczwara .
You can find such posts here and here.
How to Build a Shodan Query for Quasar
To take my analysis further, I decided to utilise the issuer information of Quasar Server CA to identify additional Quasar servers.
Shodan.io was my first choice for this investigation.
To utilise the information, I first had to build a valid query for Shodan. This was able to be done using filters list from the main shodan.io site.
The filter ssl.cert.subject.cn seemed the most appropriate. ssl.cert.issuer.cn would also work well and produce the same results in my analysis.
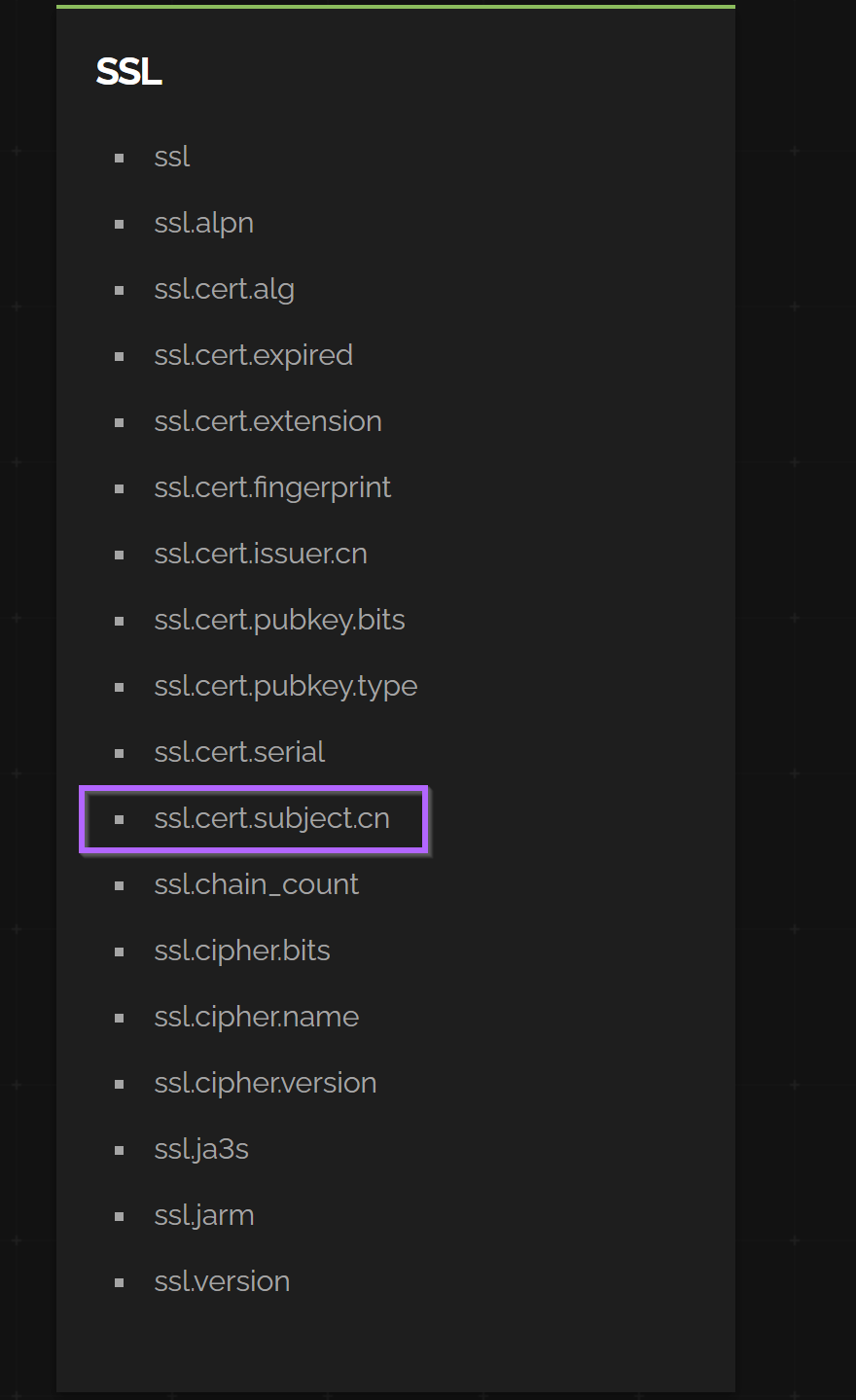
This resulted in an initial query of ssl.cert.subject.cn:"Quasar Server CA"
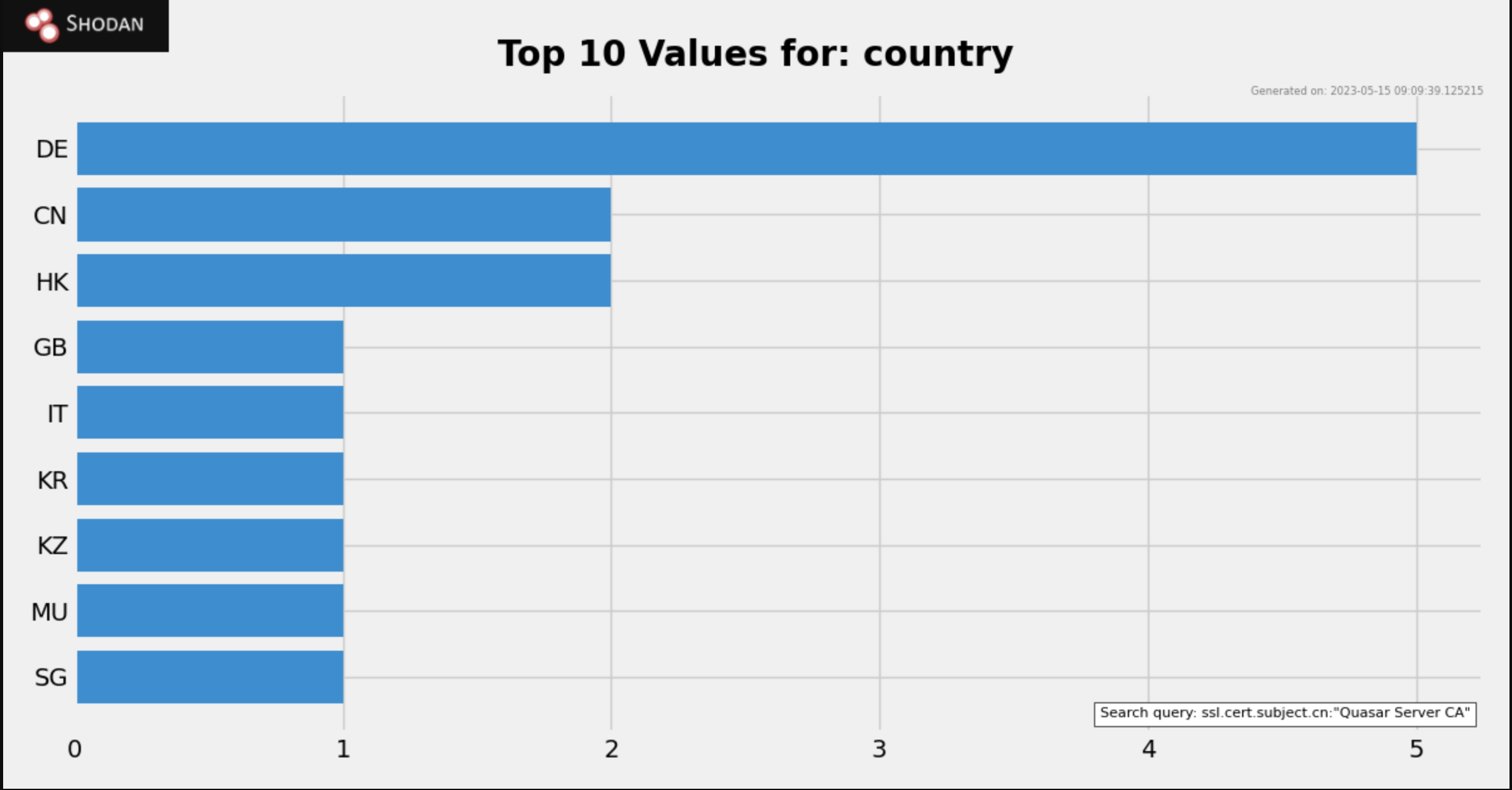
This query revealed 15 servers running with the subject common name of Quasar Server CA
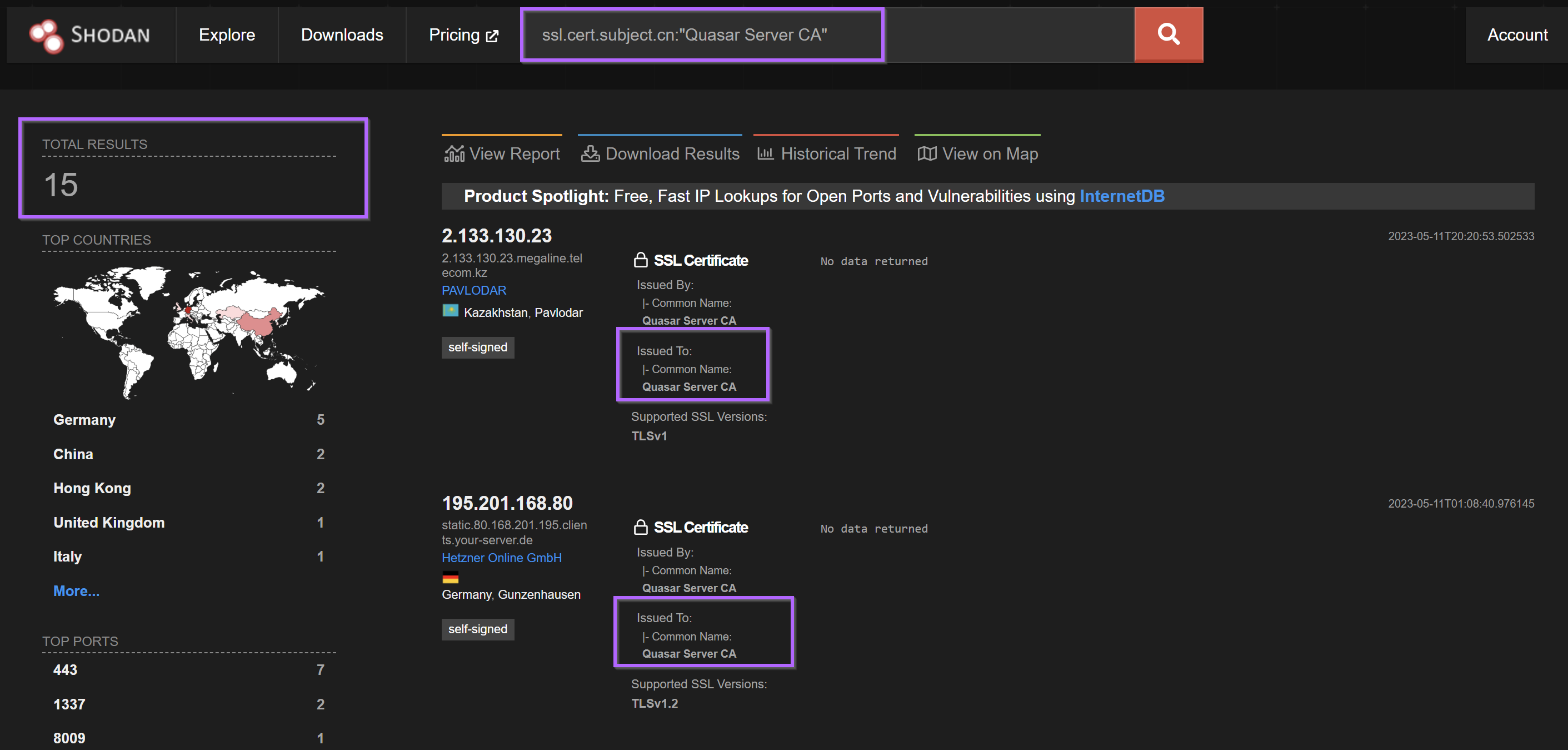
These 15 servers were geographically dispersed and primarily across China, Hong Kong and Germany. The ports used also vary and include 1337.
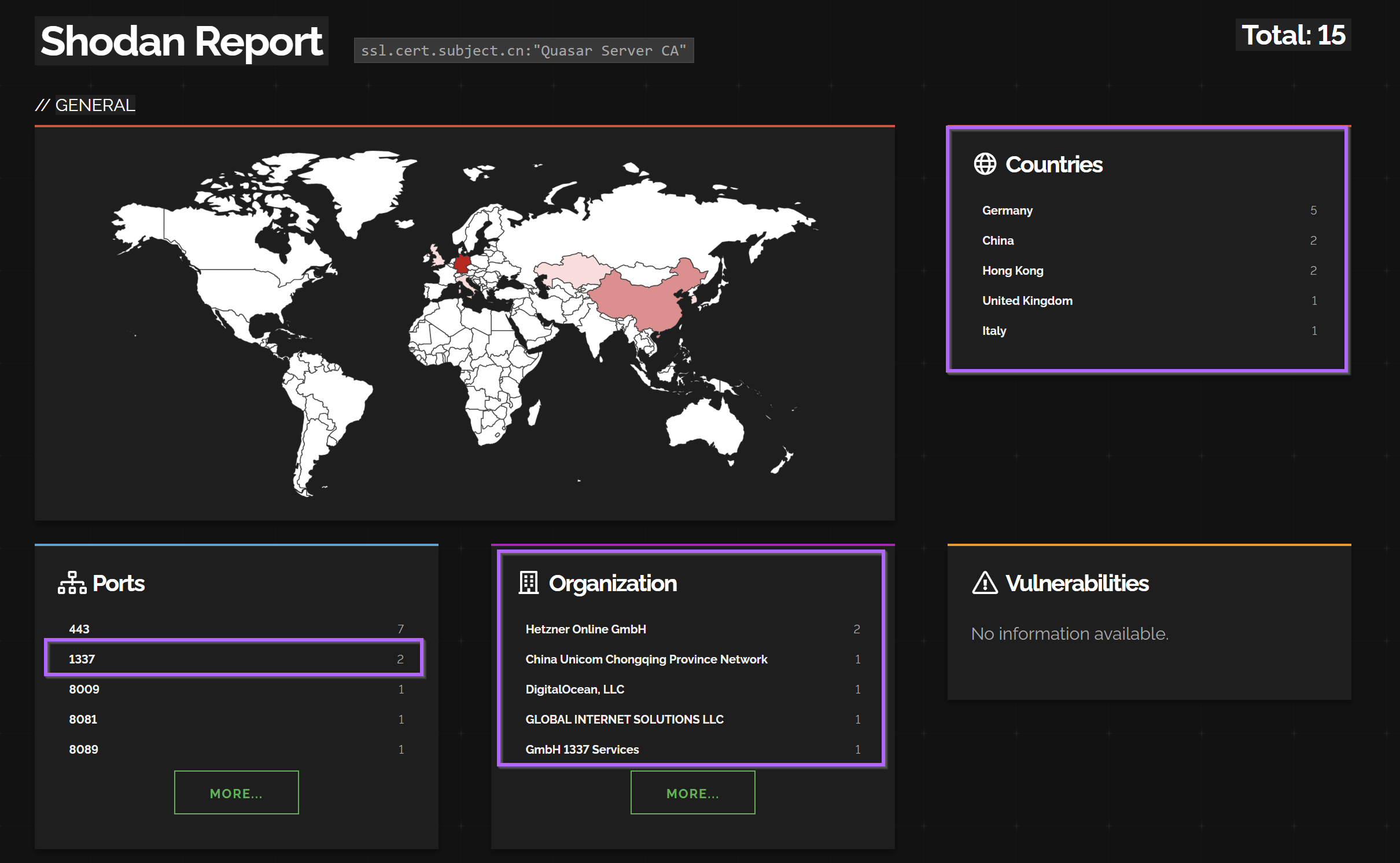
Expanding the search to hone in on port 1337.
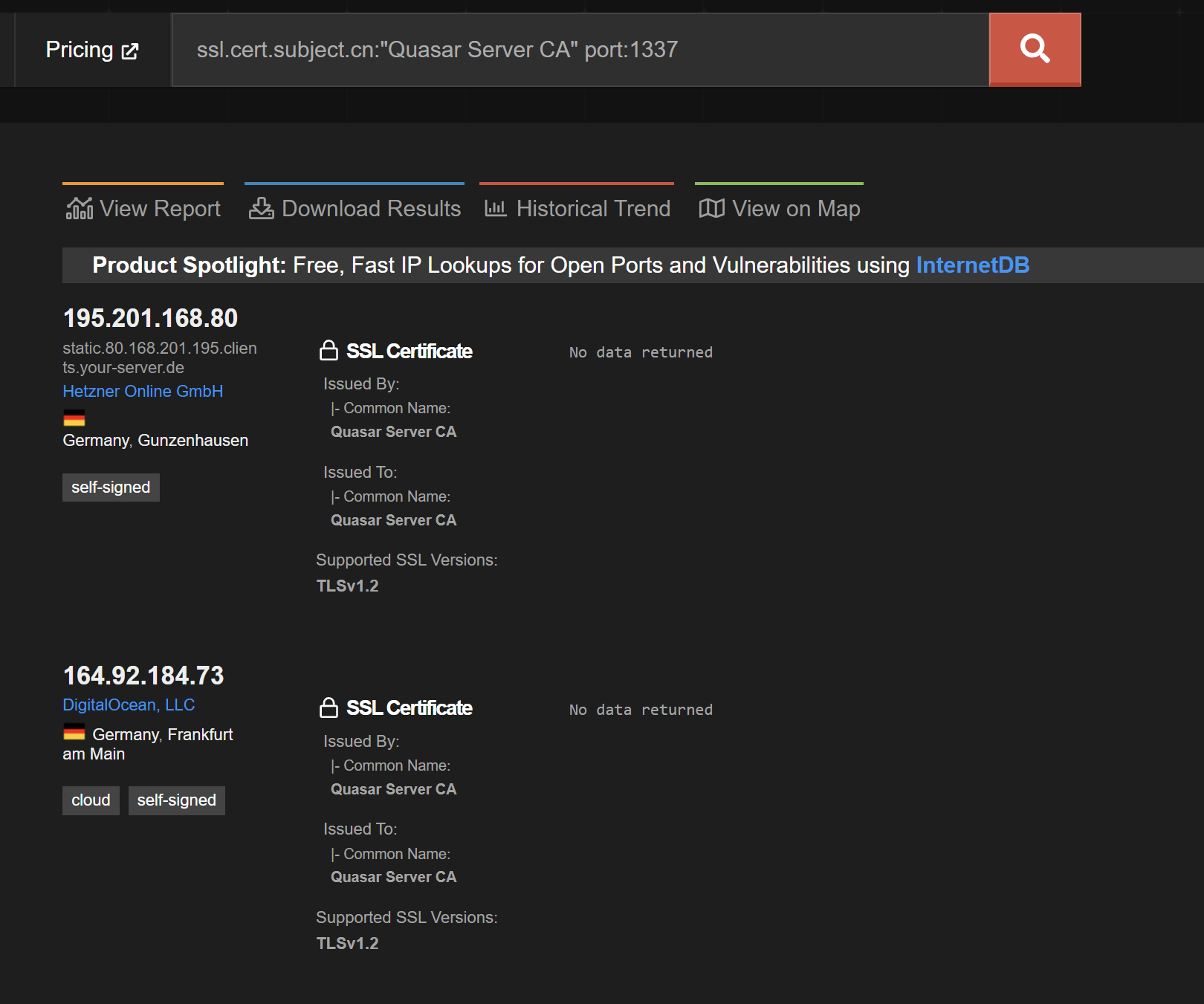
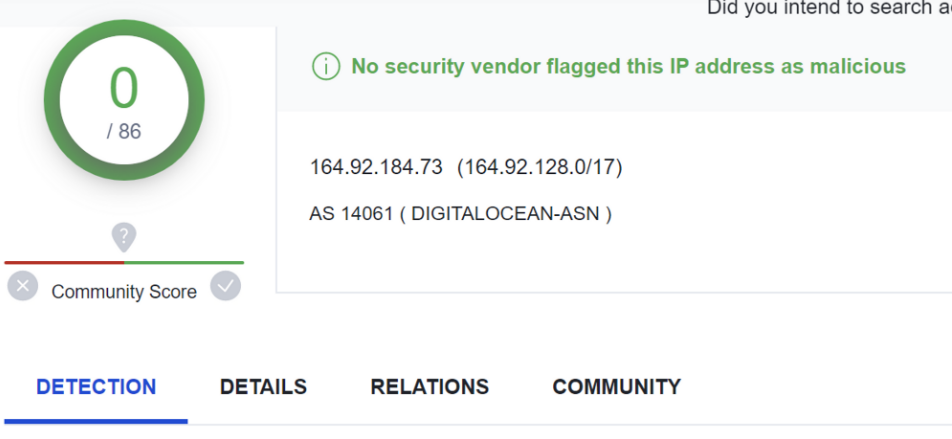
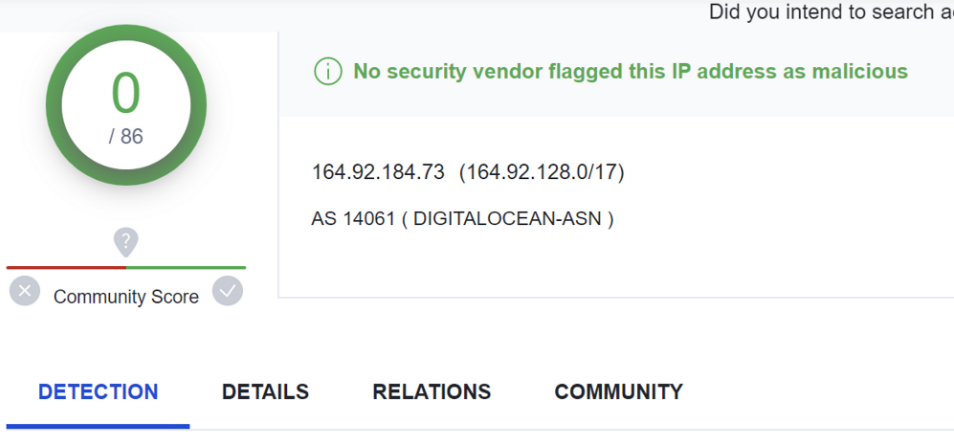
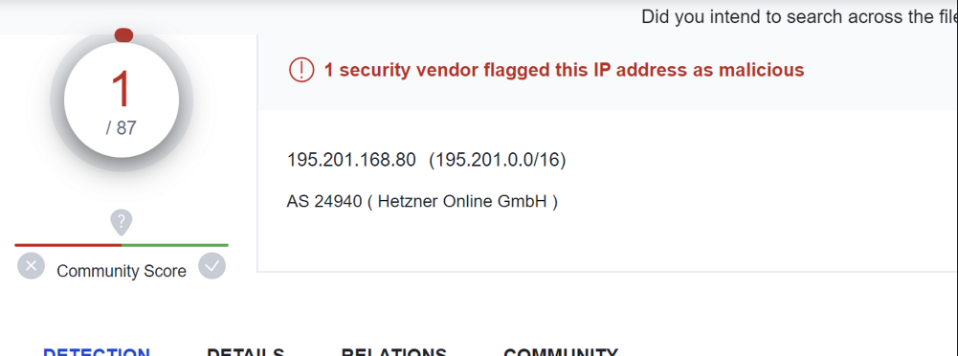
The second server of 164.92[.]184.73 had 0/86 detections on VirusTotal. The other had only 1/87 as of 2023/05/15. More information on VT detection can be found later in this article.
The servers are mostly running on cloud hosting providers. Including Hetzner, DigitalOcean and China Unicom.
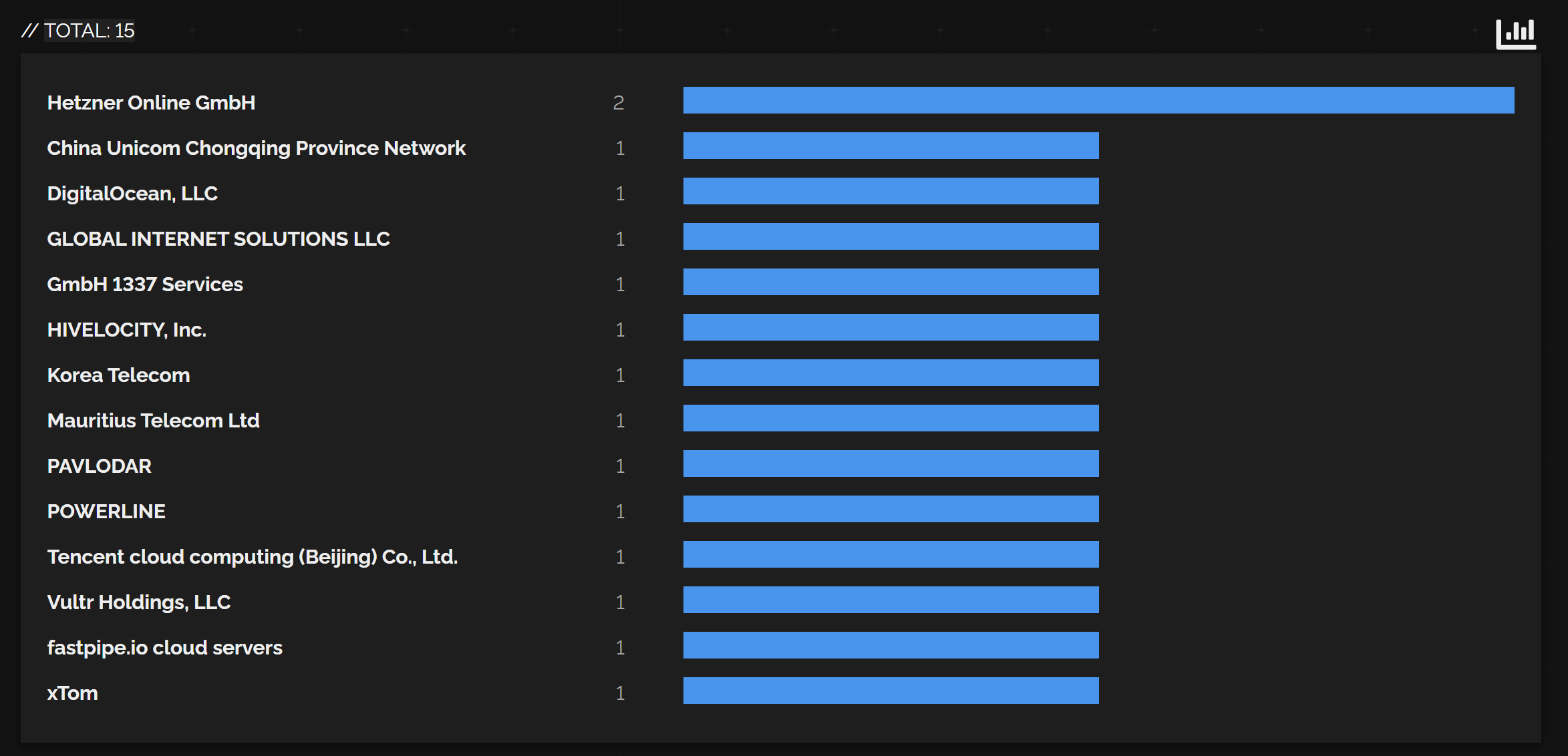
China Unicom is pretty interesting.
Another overview of the countries can be seen here.
Exporting the Full list
The rest of the shodan.io data was not extremely interesting and the associated jarm/ja3s values did not reveal much.
So I decided to export the list of servers and check the rest against VirusTotal.
A full list of the servers can be seen here.
2[.]133[.]130[.]23
27[.]11[.]235[.]246
42[.]192[.]132[.]19
43[.]240[.]48[.]46
43[.]244[.]89[.]152
45[.]32[.]106[.]94
49[.]12[.]46[.]139
59[.]26[.]93[.]6
80[.]168[.]201[.]195
81[.]19[.]141[.]35
102[.]116[.]6[.]203
139[.]46[.]12[.]49
144[.]168[.]46[.]50
152[.]89[.]244[.]43
164[.]92[.]184[.]73
180[.]235[.]137[.]45
195[.]201[.]168[.]80
198[.]244[.]160[.]119Analysing Detections Using Virustotal
Viewing the servers within VirusTotal, we can again see one of the servers running port 1337 has 0/86 detection.
The other Quasar server running 1337 has only 1/87 detections.
In total, there were 9 servers with 0 detections as of 2023-05-15. A few of these are listed below.
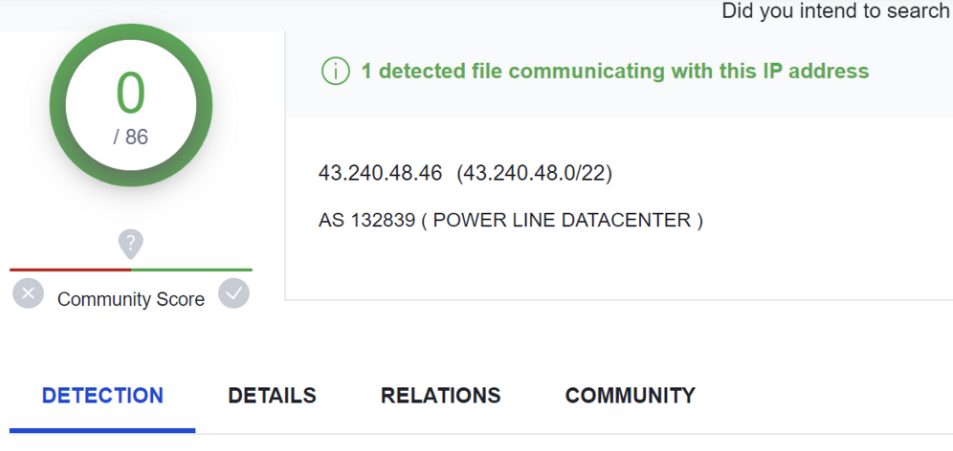
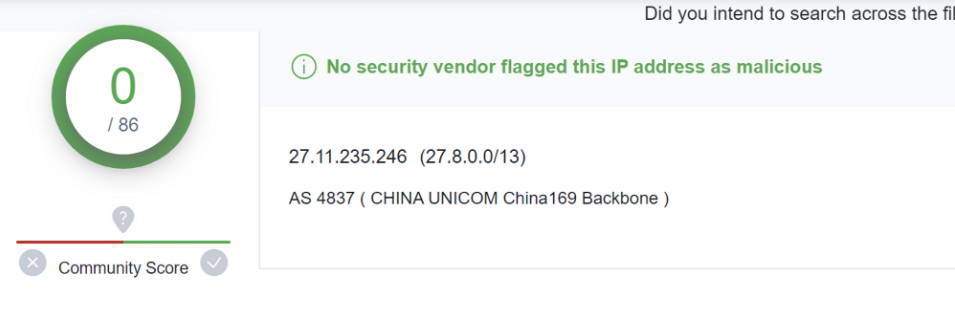
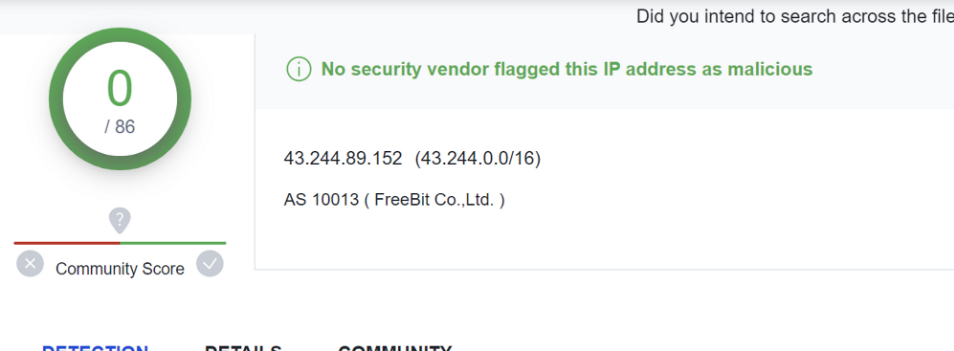
Full List of VirusTotal Detections
This is a full list of the detection rates as of 2023-05-15.
2.133.130.23 - VT 3/87
27.11.235.246 - VT 0/86
42.192.132.19 - VT 1/87
43.240.48.46 - VT 0/86
43.244.89.152 - VT 0/86
45.32.106.94 - VT 3/87
49.12.46.139 - VT 0/86
59.26.93.6 - VT 12/87
80.168.201.195 - VT 0/86
81.19.141.35 - VT 1/87
102.116.6.203 - VT 0/86
139.46.12.49 - VT 0/86
144.168.46.50 - VT 1/87
152.89.244.43 - VT 2/87
164.92.184.73 - VT 0/86
180.235.137.45 - VT 2/87
195.201.168.80 - VT 1/87
198.244.160.119 - VT 0/86Bonus Analysis Using Censys
Using Censys I was able to identify another 46 servers. I have not checked these against VirusTotal. You are welcome to do so using the full list of servers at the end of this post.
services.tls.certificates.leaf_data.subject.common_name: "Quasar Server CA"
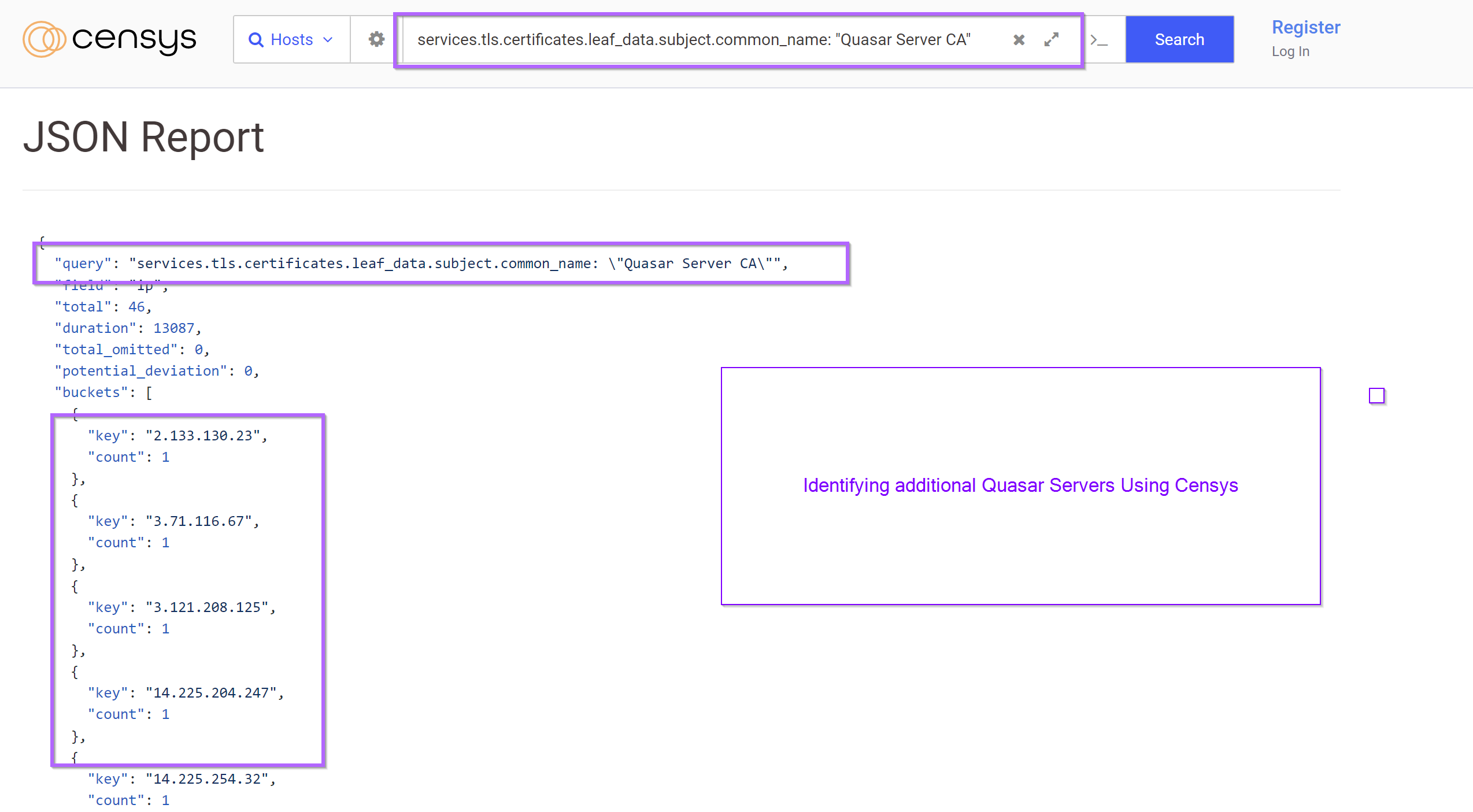
Conclusion
So it turns out malware analysis can get far more interesting beyond just C2 extraction. With minimal additional analysis, you can pivot to additional C2 infrastructure.
It's possible that some of these servers are not "malicious" per se, but I see no valid reason for using a Quasar certificate for communications. I'll assume they are all malware until notified otherwise.
Sign up for Embee Research
Malware Analysis and Threat Intelligence Research
No spam. Unsubscribe anytime.
Complete List of Quasar Infrastructure
The complete list of 64 Quasar servers.
services.tls.certificates.leaf_data.subject.common_name: "Quasar Server CA"
102.116.6.203
111.90.148.240
139.180.219.18
139.46.12.49
14.225.204.247
14.225.254.32
144.168.46.50
146.70.113.150
146.70.172.107
147.182.226.65
152.89.244.43
164.92.184.73
172.174.58.11
180.235.137.45
185.219.134.204
185.235.128.46
185.80.128.131
188.173.86.162
194.55.224.25
194.58.188.72
195.201.168.80
198.244.160.119
2.133.130.23
20.123.197.130
20.231.104.157
207.32.218.112
209.25.142.223
212.227.45.37
212.90.103.114
222.106.112.206
27.11.235.246
3.121.208.125
3.71.116.67
34.96.240.37
42.192.132.19
43.154.232.190
43.240.48.46
43.244.89.152
45.12.213.244
45.32.106.94
45.80.158.187
45.88.107.55
47.242.113.51
47.242.167.217
47.243.141.95
47.243.172.172
49.12.46.139
51.75.52.3
52.204.66.30
59.26.93.6
61.4.115.124
61.4.115.99
70.176.21.36
73.90.120.173
77.34.128.25
80.168.201.195
81.19.141.35
85.31.45.38
91.192.100.36
222.106.112.206
Complete List with Port Numbers
102.116.6.203:8009
108.160.136.232:8088
111.90.148.240:8088
116.36.143.105:8888
139.180.219.18:8088
14.225.204.247:6060
14.225.254.32:9090
144.168.46.50:9000
146.70.113.150:8443
146.70.172.107:55442
147.182.226.65:9702
152.89.244.43:443
164.92.184.73:1337
180.235.137.45:9443
180.235.137.45:9443
185.219.134.204:54321
185.219.176.42:1337
185.235.128.46:4022
185.80.128.131:12121
188.173.86.162:4873
194.55.224.25:25
194.58.188.72:8543
195.201.168.80:1337
195.201.168.80:1337
198.244.160.119:443
2.133.130.23:443
2.133.130.23:443
20.123.197.130:8080
20.231.104.157:6666
207.32.218.112:4782
209.25.142.223:23508
212.227.45.37:80
212.23.222.42:7331
212.90.103.114:5431
222.106.112.206:1297
27.11.235.246:8089
3.121.208.125:1337
3.71.116.67:4567
34.96.240.37:6443
42.192.132.19:8443
43.154.232.190:8442
43.240.48.46:443
45.12.213.244:4499
45.32.106.94:8080
45.32.106.94:8081
45.32.110.240:8080
45.80.158.187:3577
45.88.107.55:4499
47.242.113.51:8442
47.242.167.217:12199
47.243.141.95:5672
47.243.172.172:16099
49.12.46.139:443
52.204.66.30:443
59.26.93.6:443
61.4.115.124:6699
61.4.115.99:6699
70.176.21.36:7331
74.207.237.228:8877
77.34.128.25:8080
81.19.141.35:443
81.19.141.35:443
85.31.45.38:6969
91.192.100.36:8084