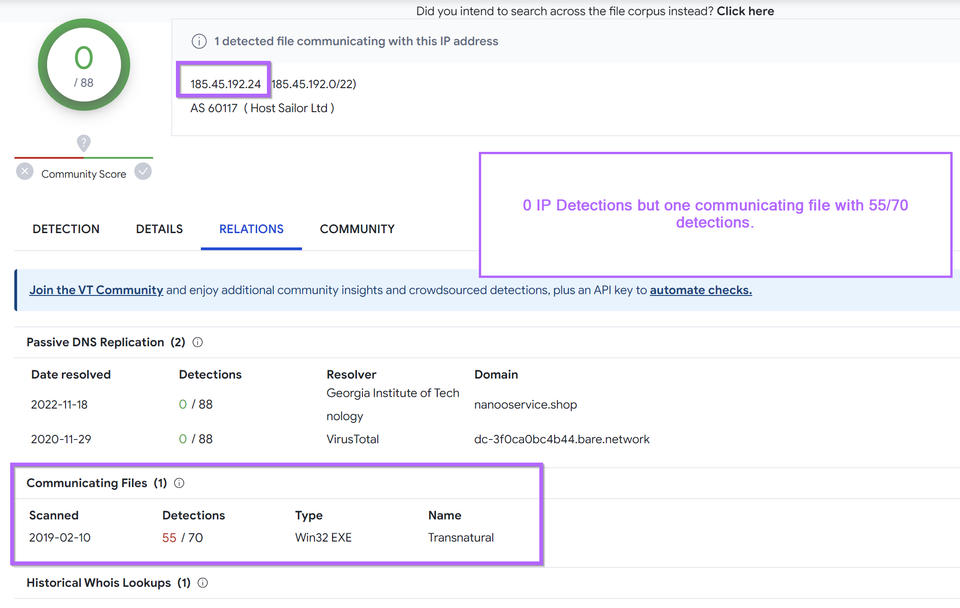
Censys
Threat Intelligence
|
Nov 22, 2023
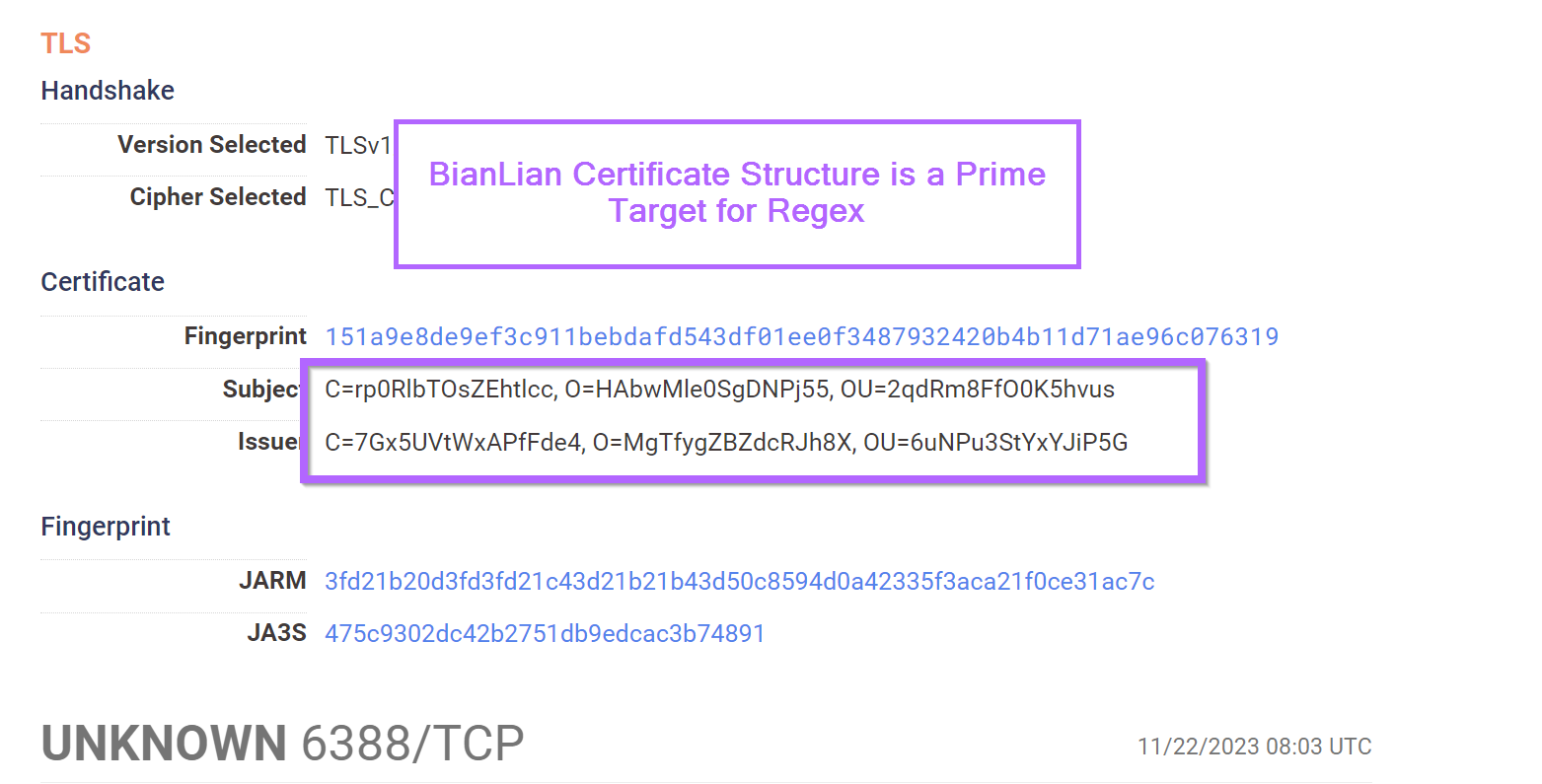
More interesting and practical queries for identifying malware infrastructure.
Threat Intelligence
|
Nov 19, 2023
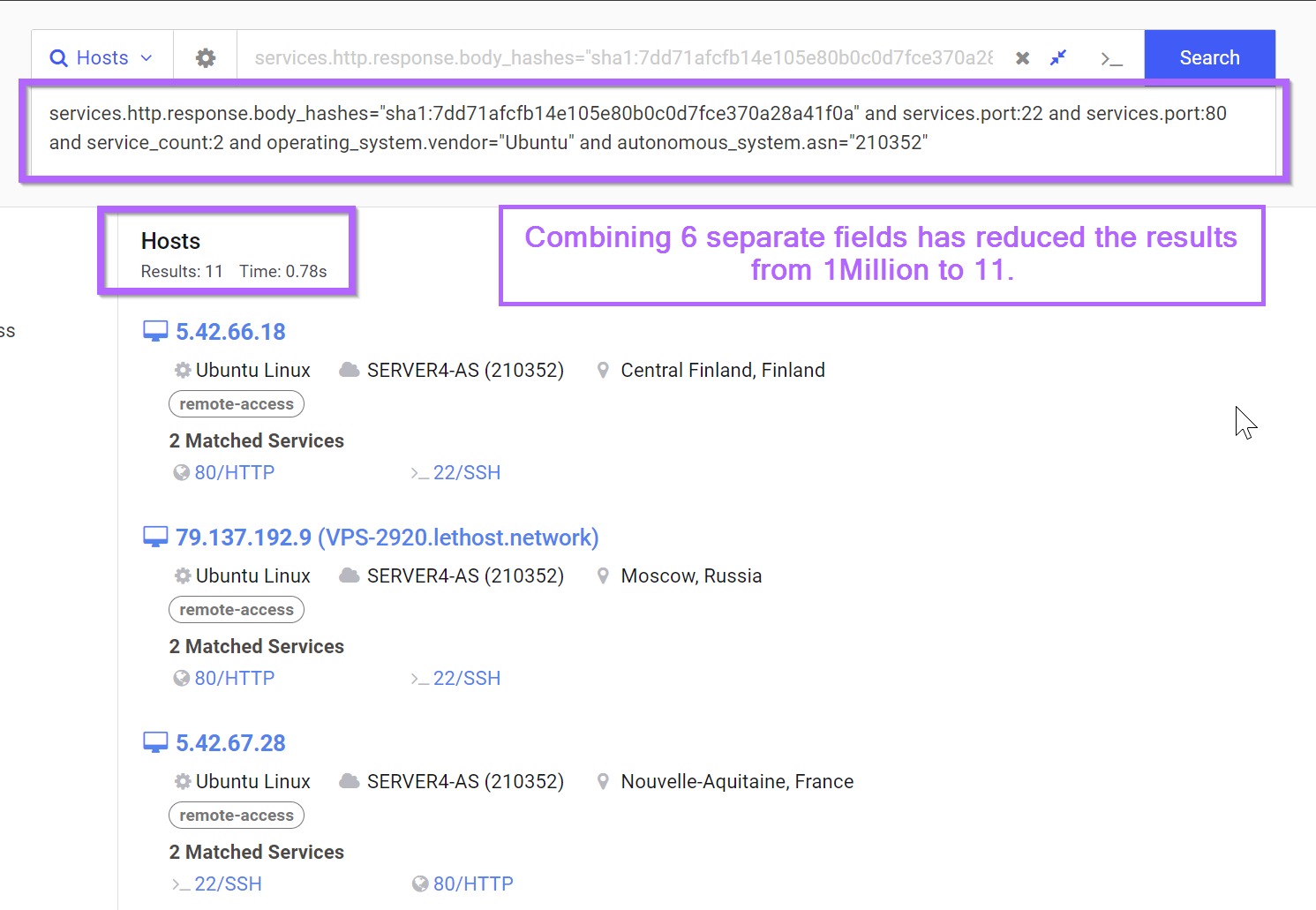
Identifying Malware infrastructure by combining weak pivot points.
Threat Intelligence
|
Nov 15, 2023
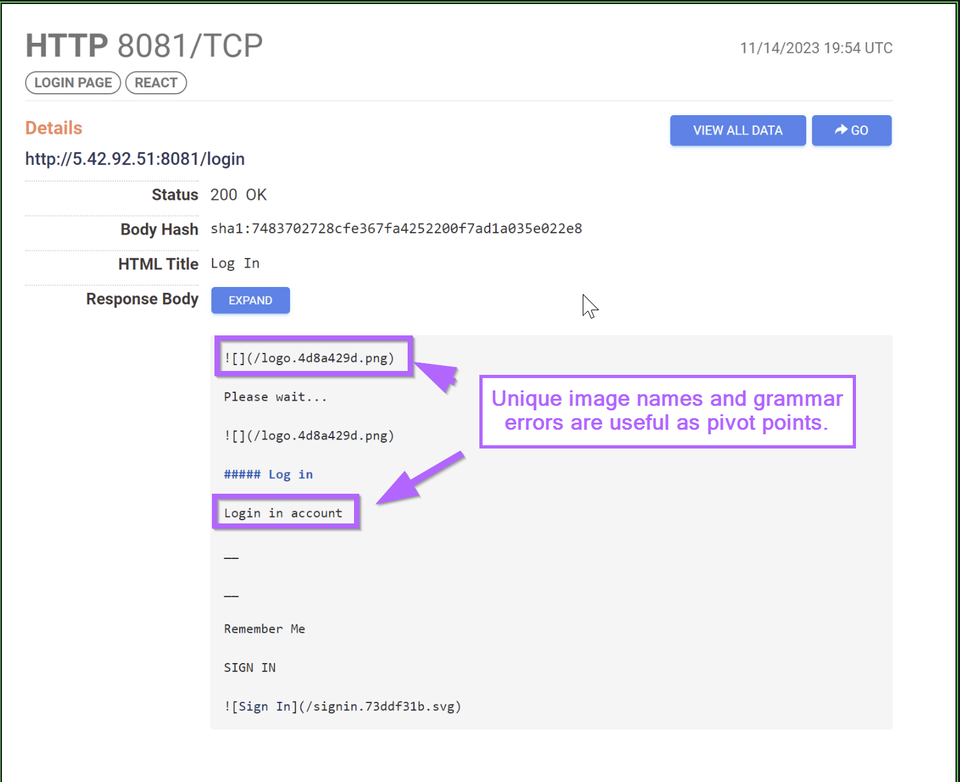
Identifying Simple pivot points in RisePro Stealer Infrastructure using Censys.