In a previous post we analysed a Redline stealer sample and obtained a C2 address of 5.42.92[.]51:19057.
In this post, we'll demonstrate how to pivot from this c2 address to identify a total of 16 additional related servers.
Initial Search With Censys
We can begin by performing a basic search for the c2 on Censys.
This search reveals some basic information such as running services, ASN and the location of the server.
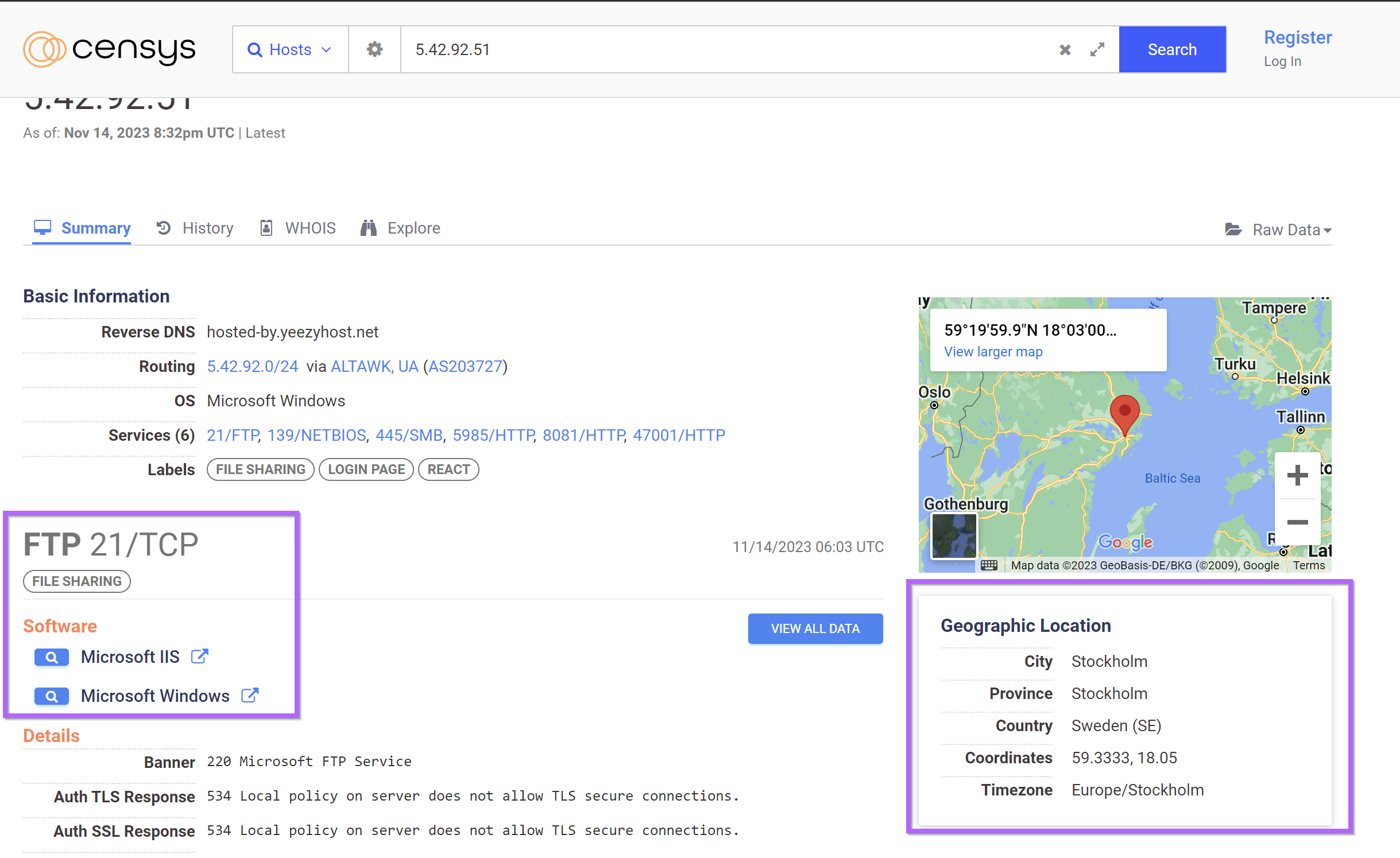
The initial services do not appear to be useful, there isn't much to pivot from on ports on ports 21,139,445 and 5985
However, there is an interesting HTTP service running on port 8081.
This service appears to be hosting a login panel. (These panels are self hosted by RisePro users, according to this report from FlashPoint)
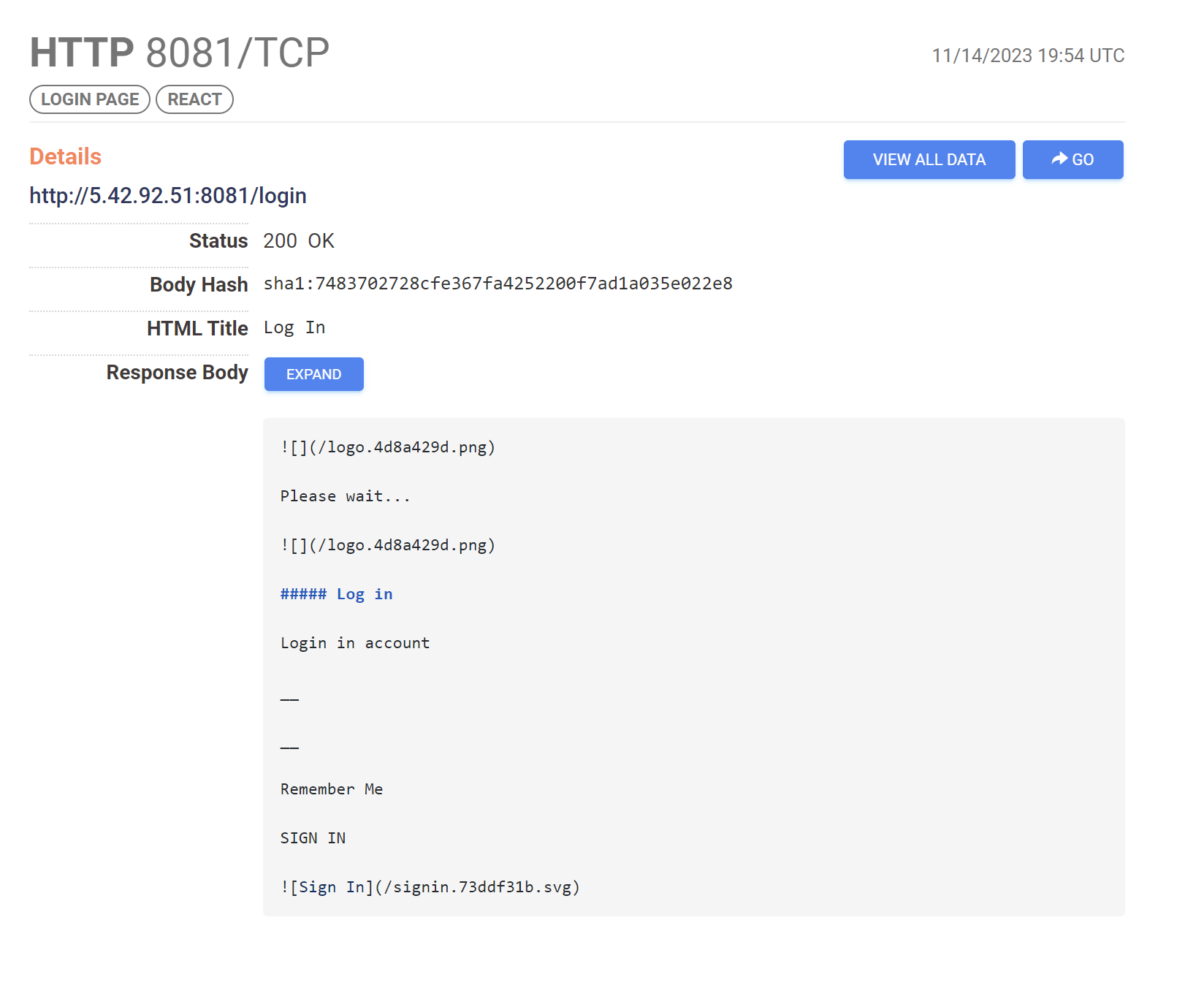
This HTTP service is interesting and contains multiple opportunities for pivoting to additonal servers.
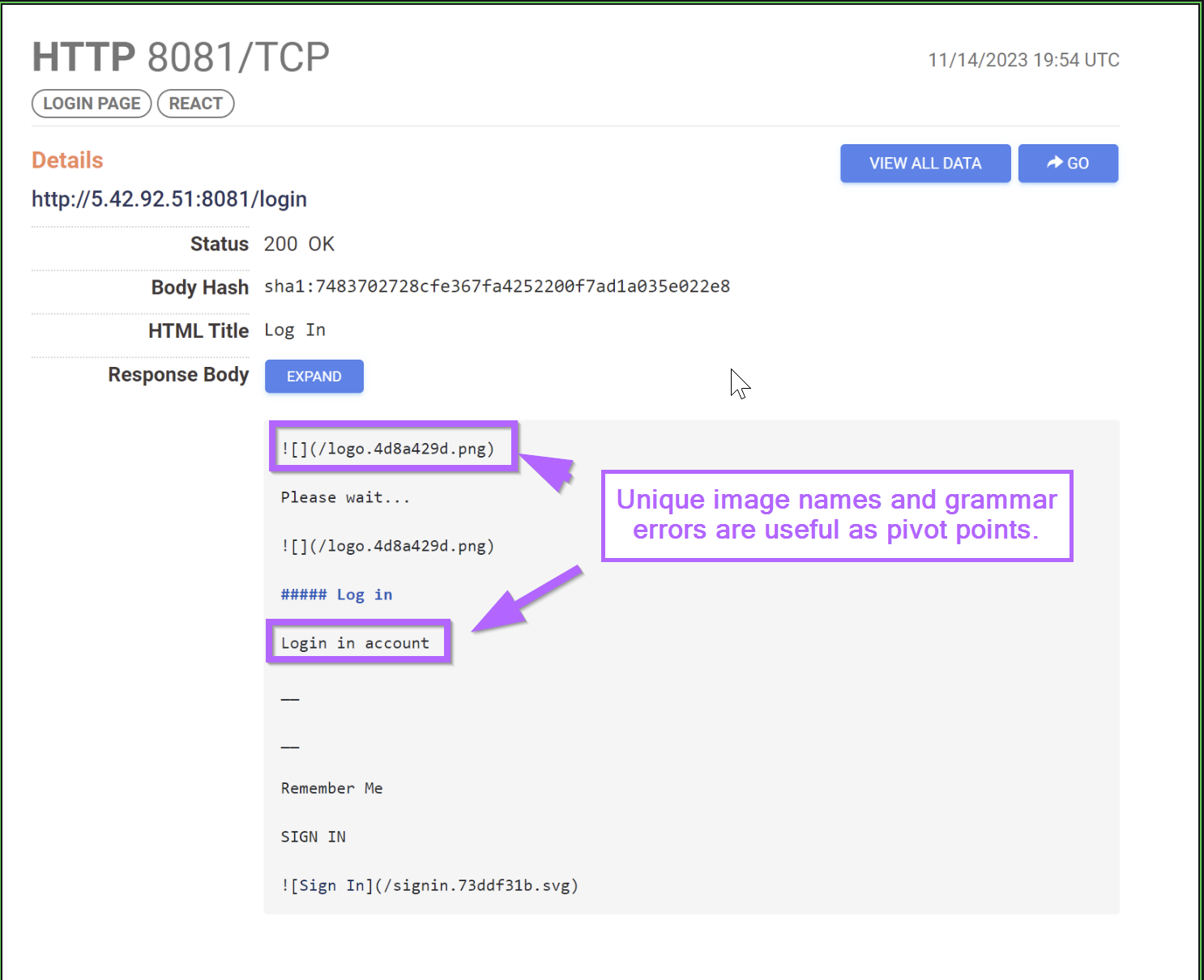
Opportunity 1: Pivoting With Image Names
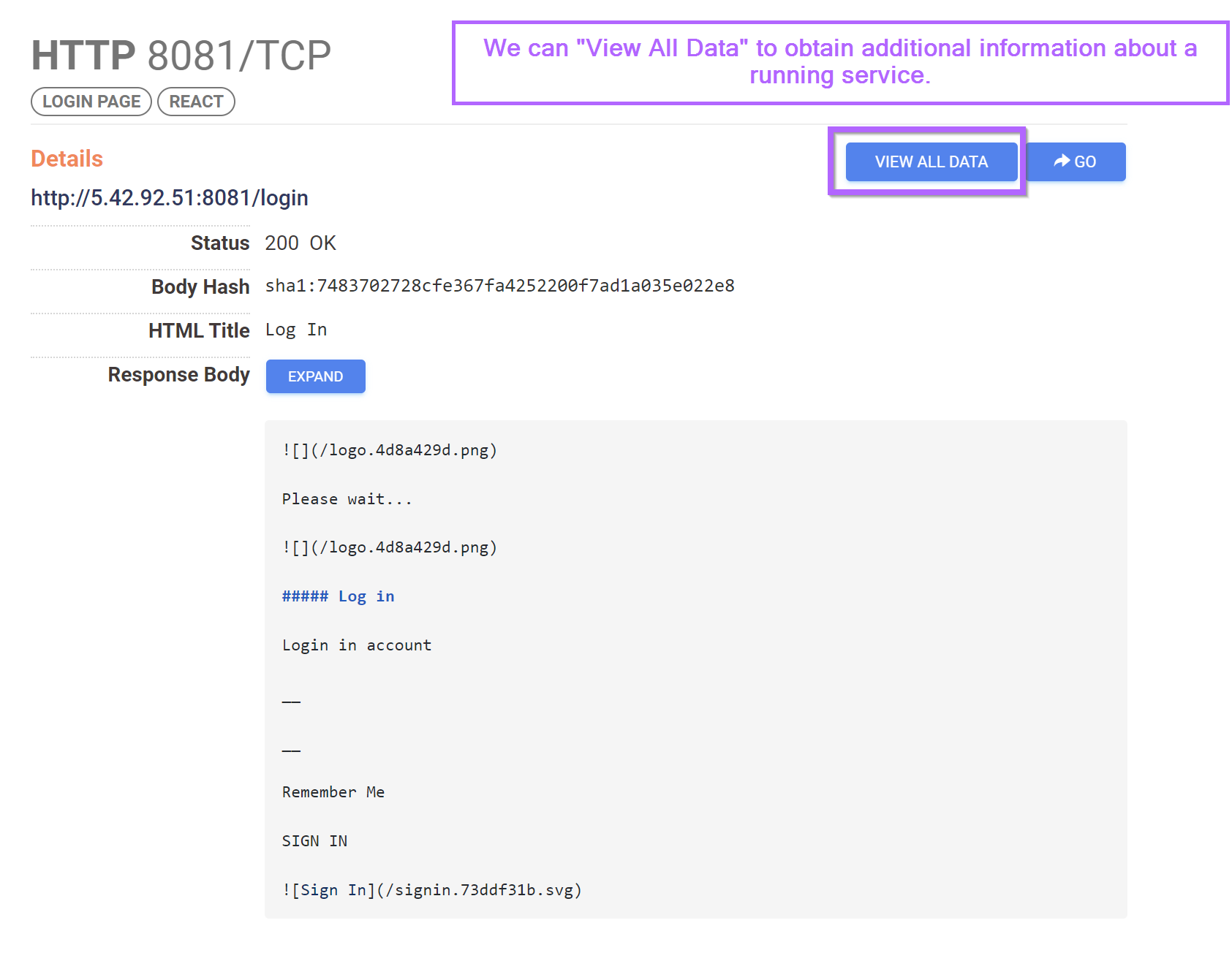
Within the screenshot above, we can see some raw html of the login page.
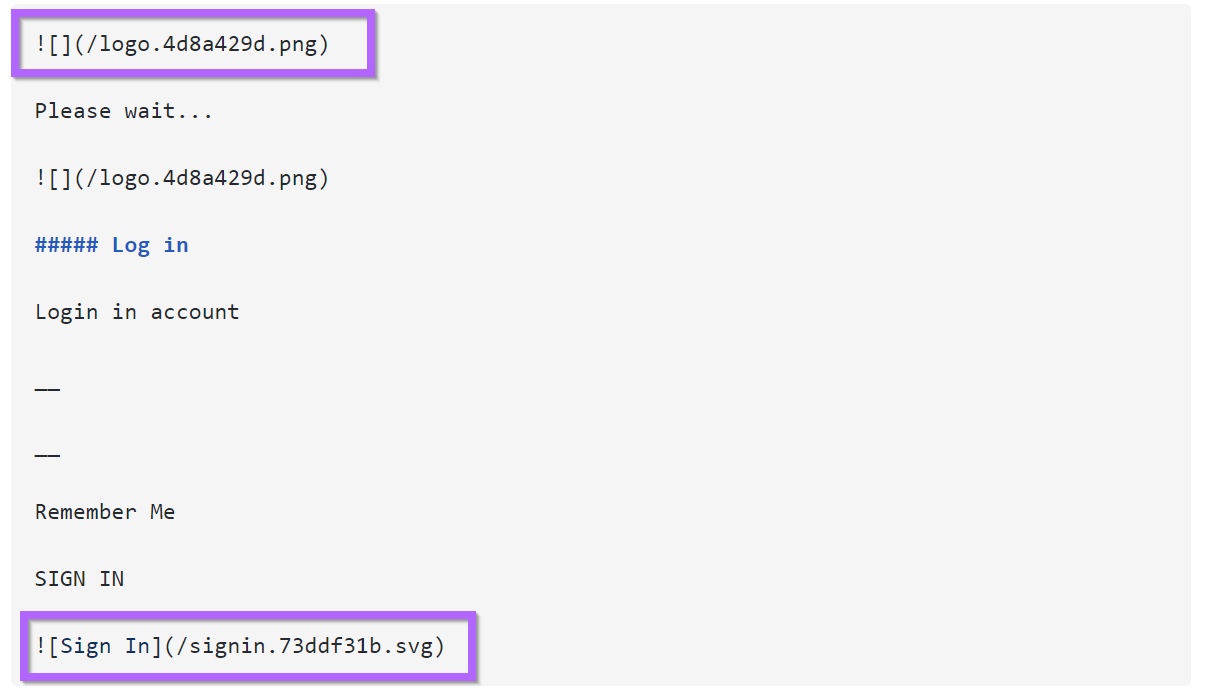
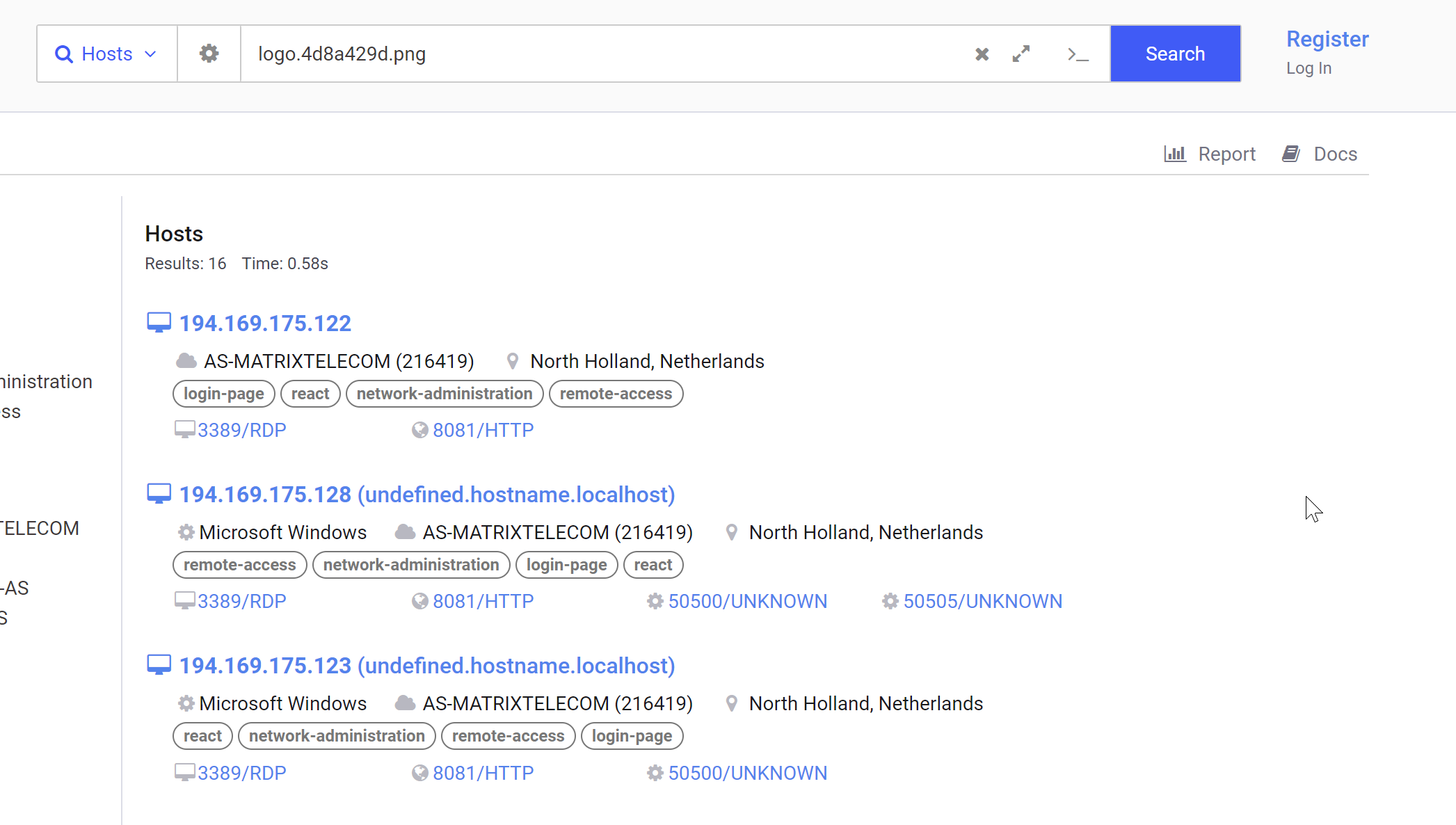
Looking closely, we can see some relatively unique names used for the .png and .svg images.
By plugging either of these names into a Censys search, there are a total of 16 servers identified.
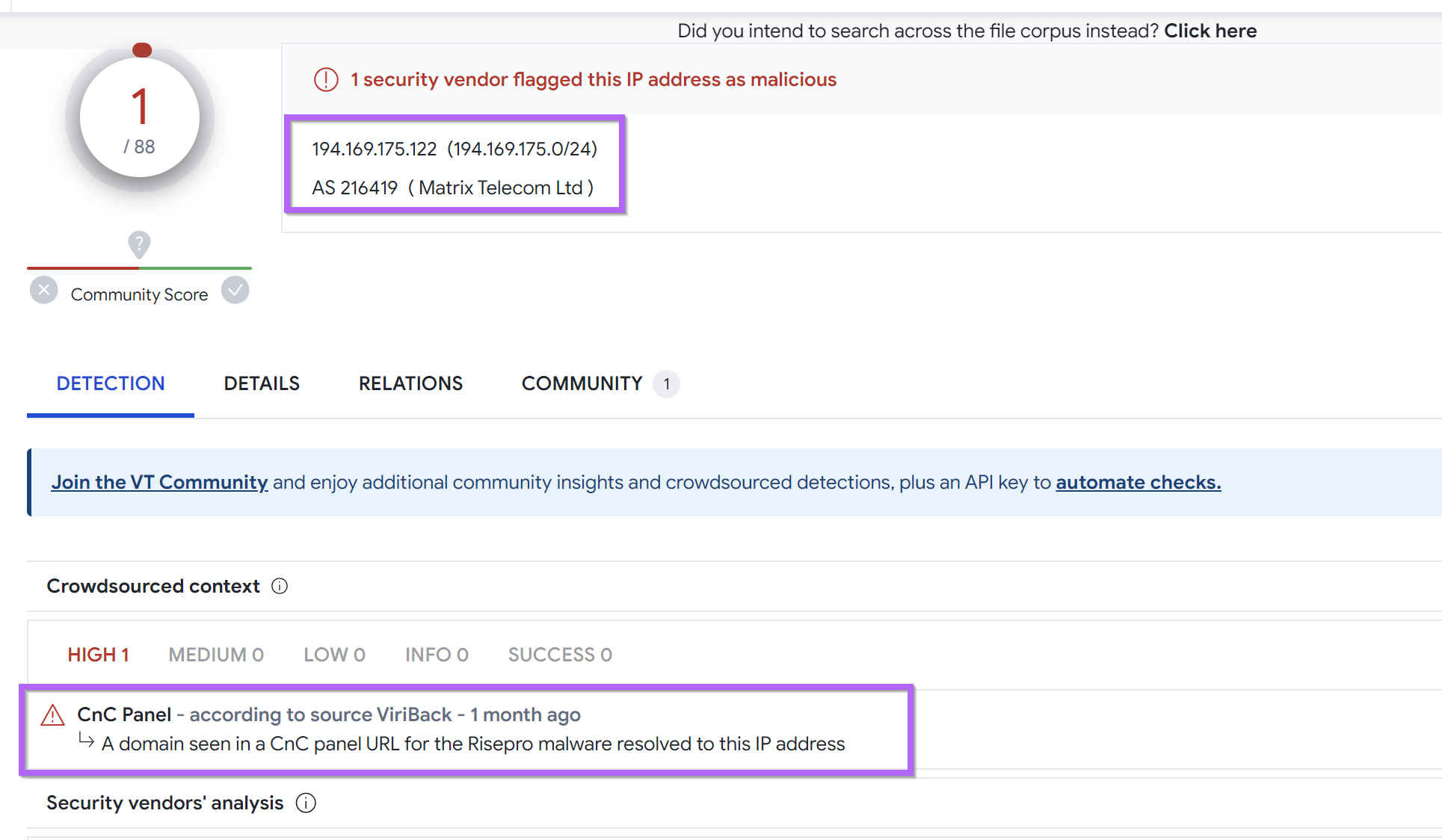
We can take the first returned IP of 194.169.175[.]122 and search for it in Virustotal.
This returns 1/88 detections, as well as a reference to Risepro malware. (Similar results can be obtained for most the remaining 15 servers)
Opportunity 2: Pivoting With Banner Hash
Censys is able to obtain a significant amount of information about the running service, some of which is not displayed by default.
We can view this additional information by clicking on "View All Data".
This returns a lot of information about the running service on port 8081.
Each piece of information can be searched by clicking on the "search" box next to each option.
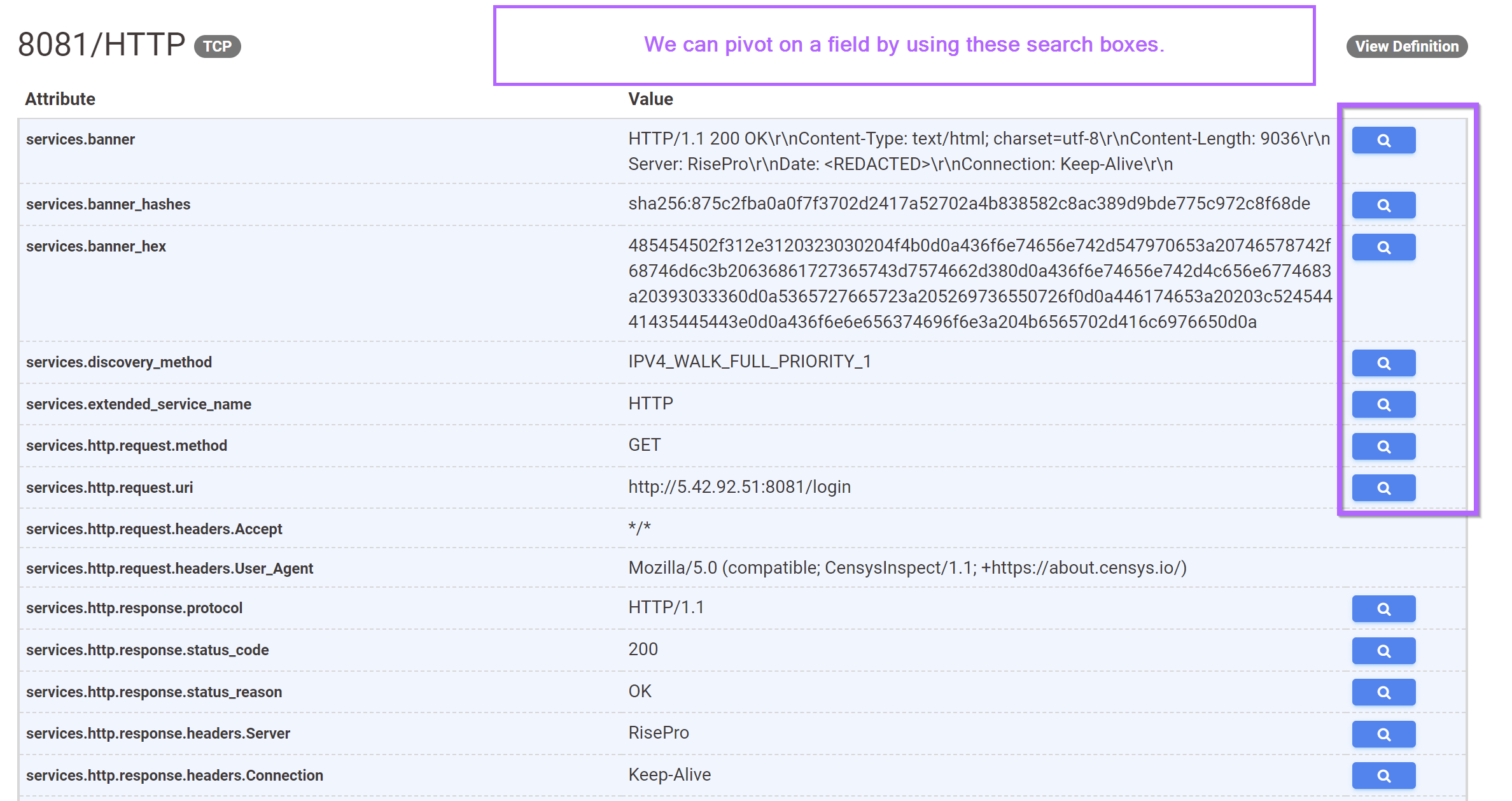
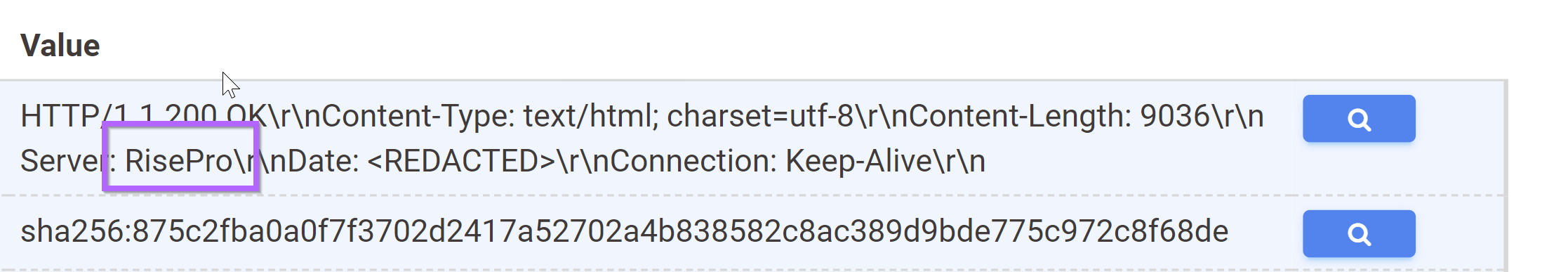
For example, we can click on the services.banner_hashes search box to attempt a pivot from a hash of the banner, which contains a reference to "RisePro".
Pivoting on the banner hash returns 3 results.
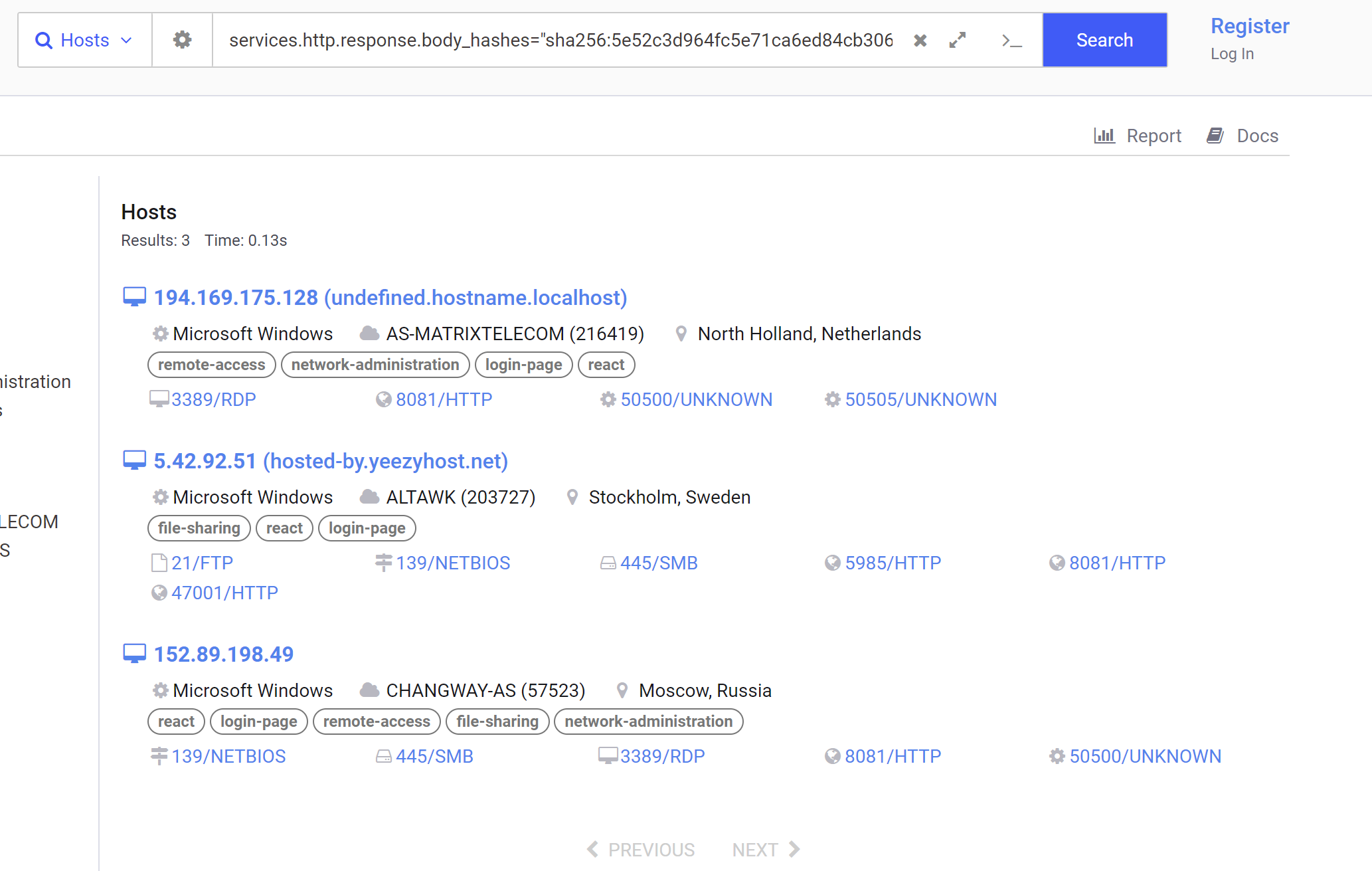
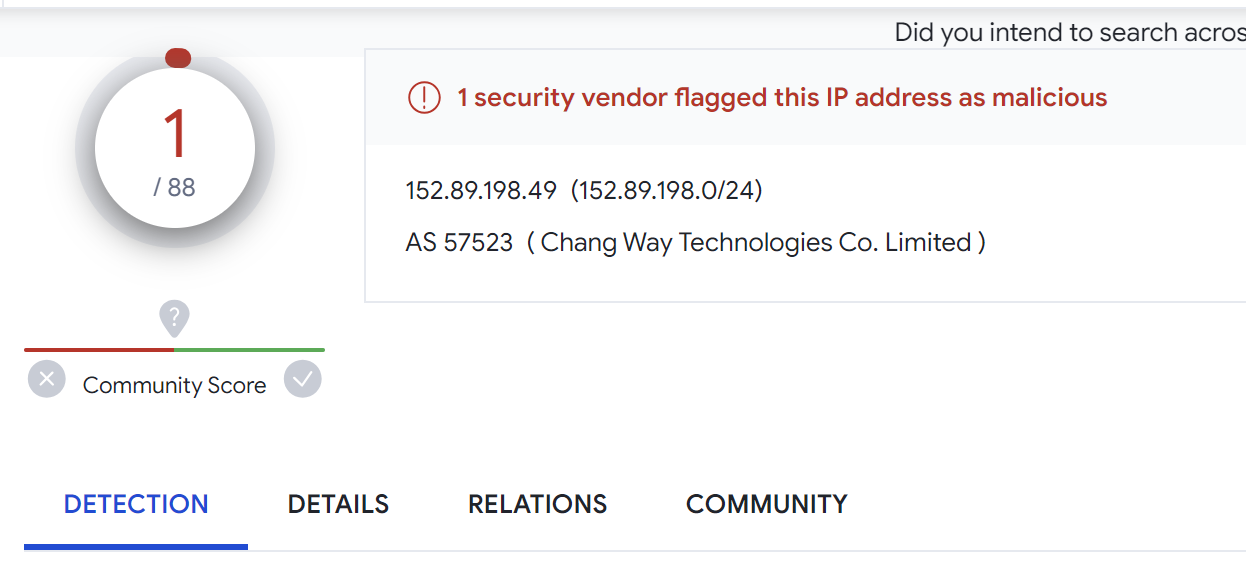
Of the results is a new IP of 152.89.198[.]49. Which has 1/88 detections on Virustotal.
Opportunity 3: Pivoting From RisePro String
The previous search using banner hashes only returned 3 results.
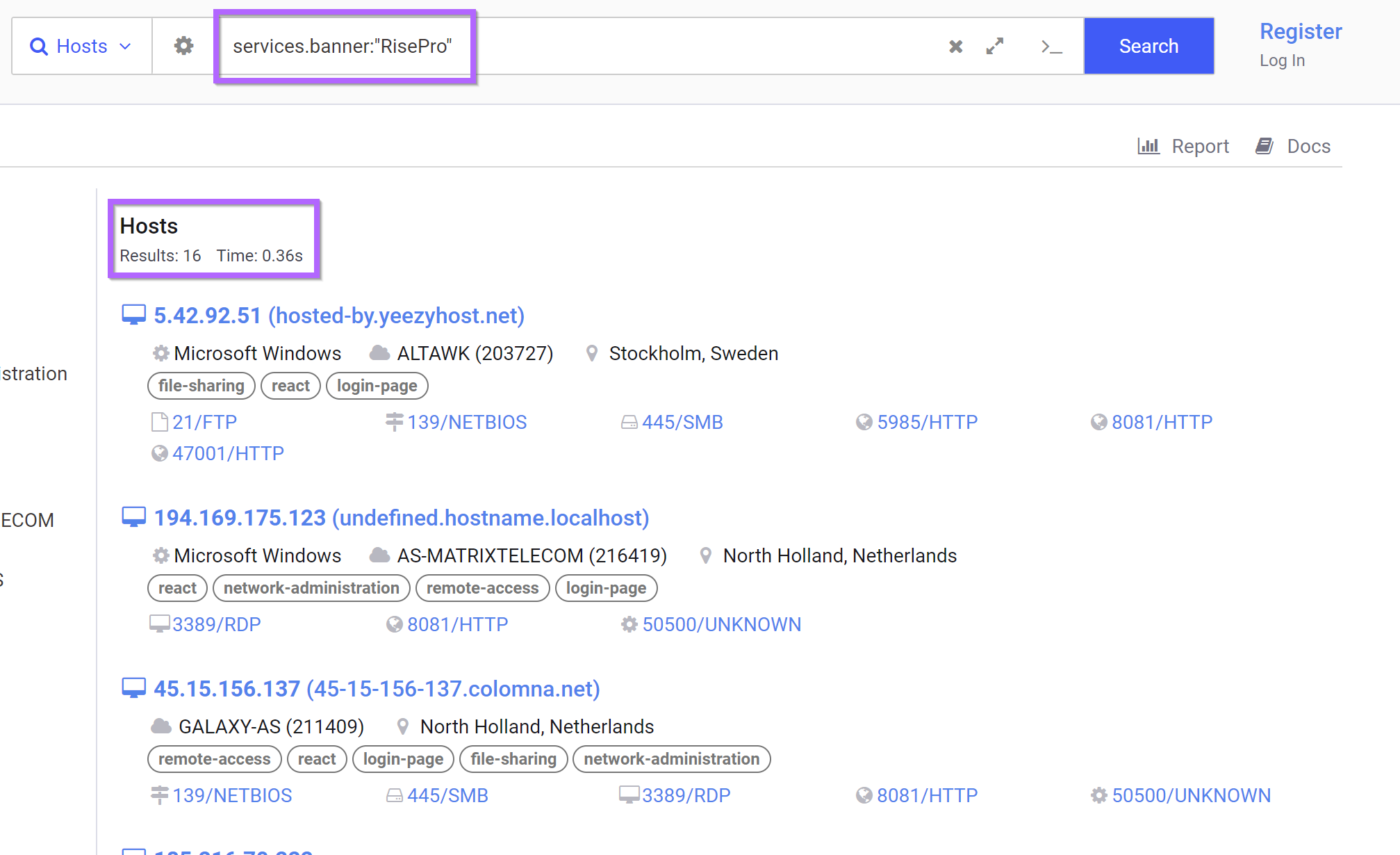
Since the most interesting piece of the banner is the reference to "RisePro", we can skip using the hash and instead look for any banner with a RisePro reference.
By searching for any banner containing a reference to "RisePro", we can obtain the same 16 results that were obtained by pivoting on the .png image name.
Opportunity 4: Pivoting From Grammatical Errors
There is a small grammatical error contained in the initial html.
If we assume that this error is present across login panels, then we can use it as an additional pivot point.
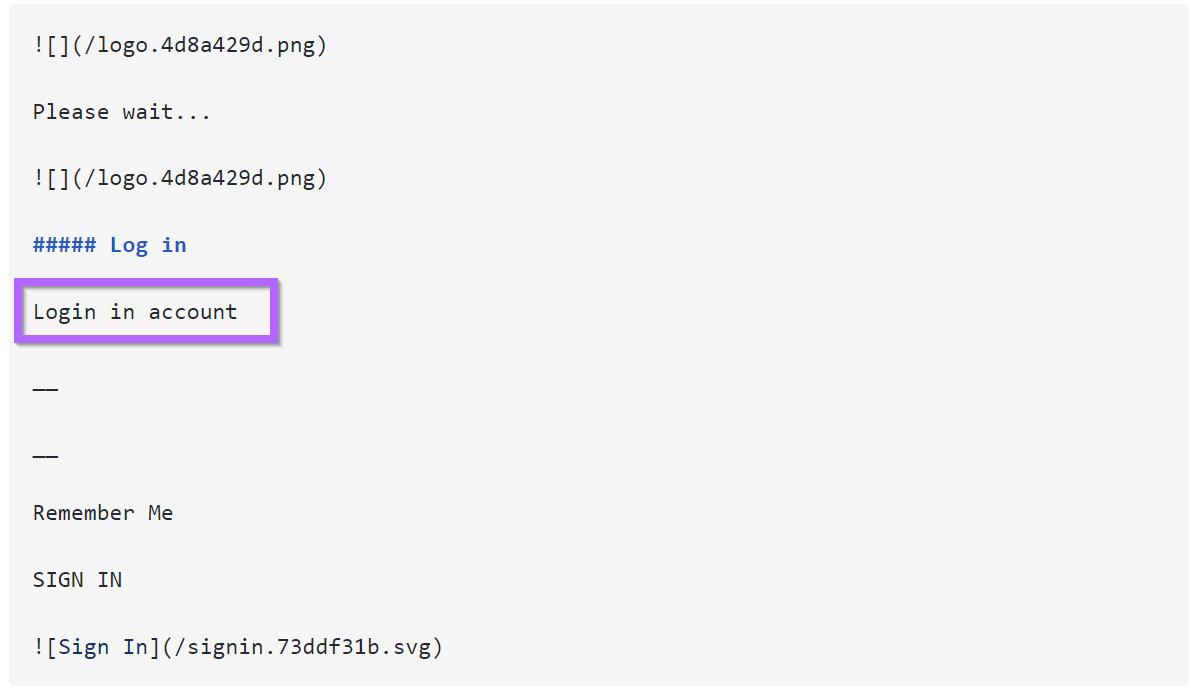
By searching for the error inside of the response body, we can again obtain the same 16 results, as well as one additional server.
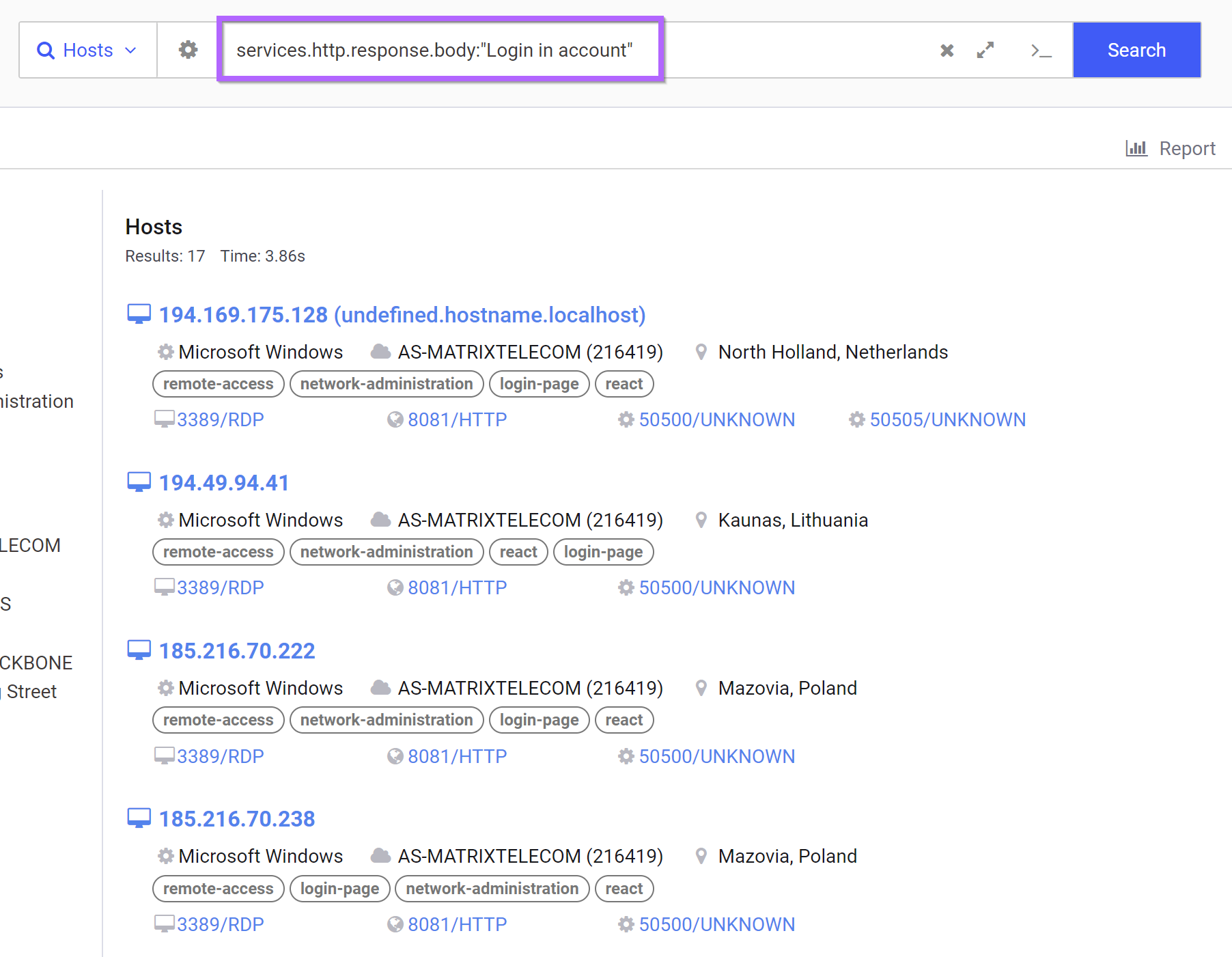
The additional server has an ip of 61.134.65[.]198 and appears to be a chinese site unrelated to RisePro.
Despite the 1 additional false positive, the remaining 16 results appear malicious and related to RisePro Stealer. This confirms that the grammar error is useful as an additional pivot point.
Basic Analysis of Newly Identified Servers
Using the 16 RisePro servers returned from our search, there are some interesting observations.
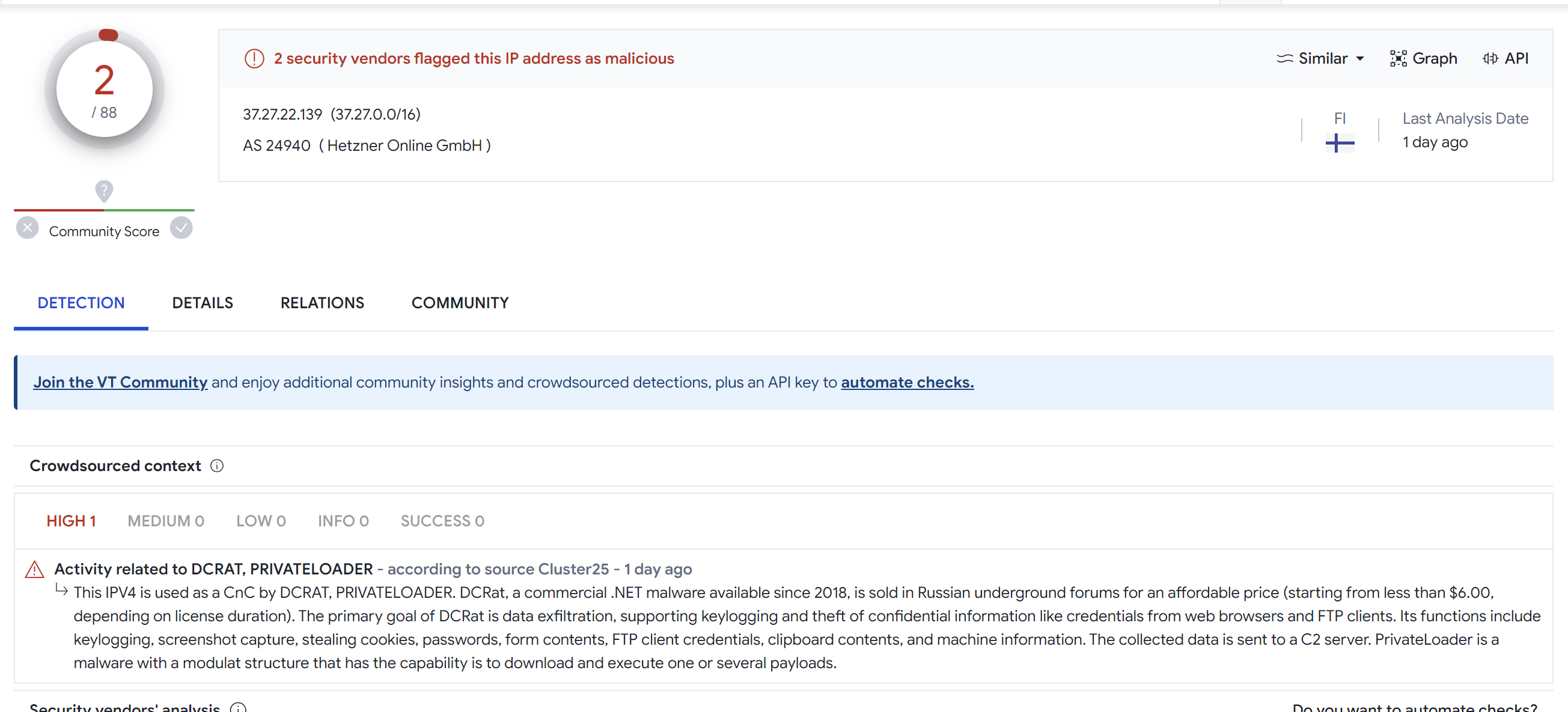
Here is an example where 37.27.22[.]139 is marked as "DCRAT,PRIVATELOADER" and yet only has 2/88 detections.
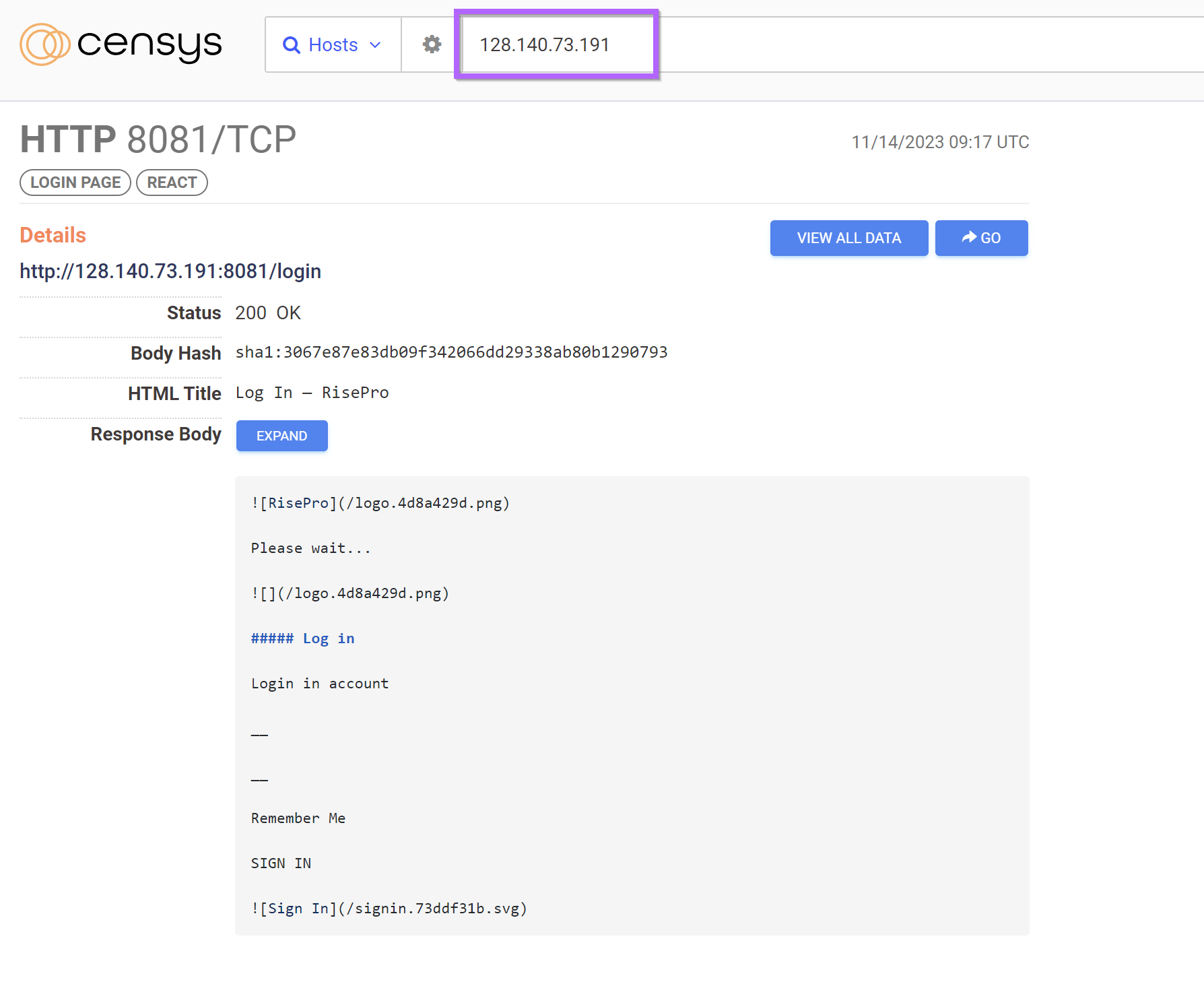
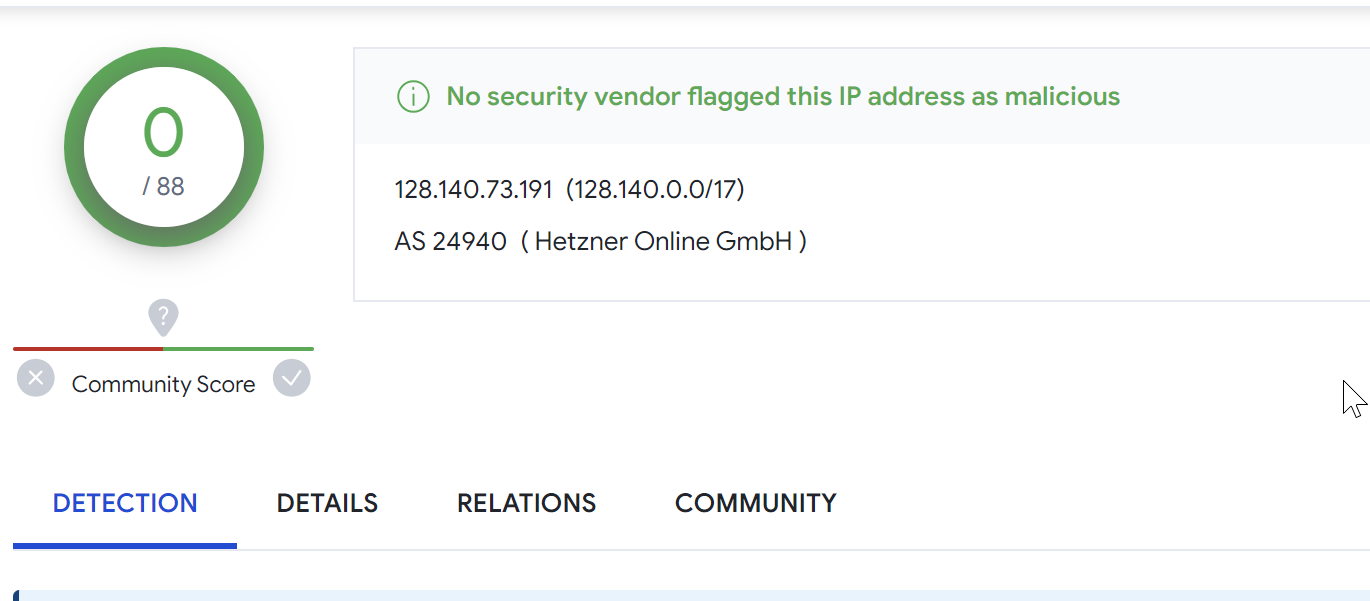
Another server 128.140.73[.]191 contains the same C2 panel and has 0/88 detections.
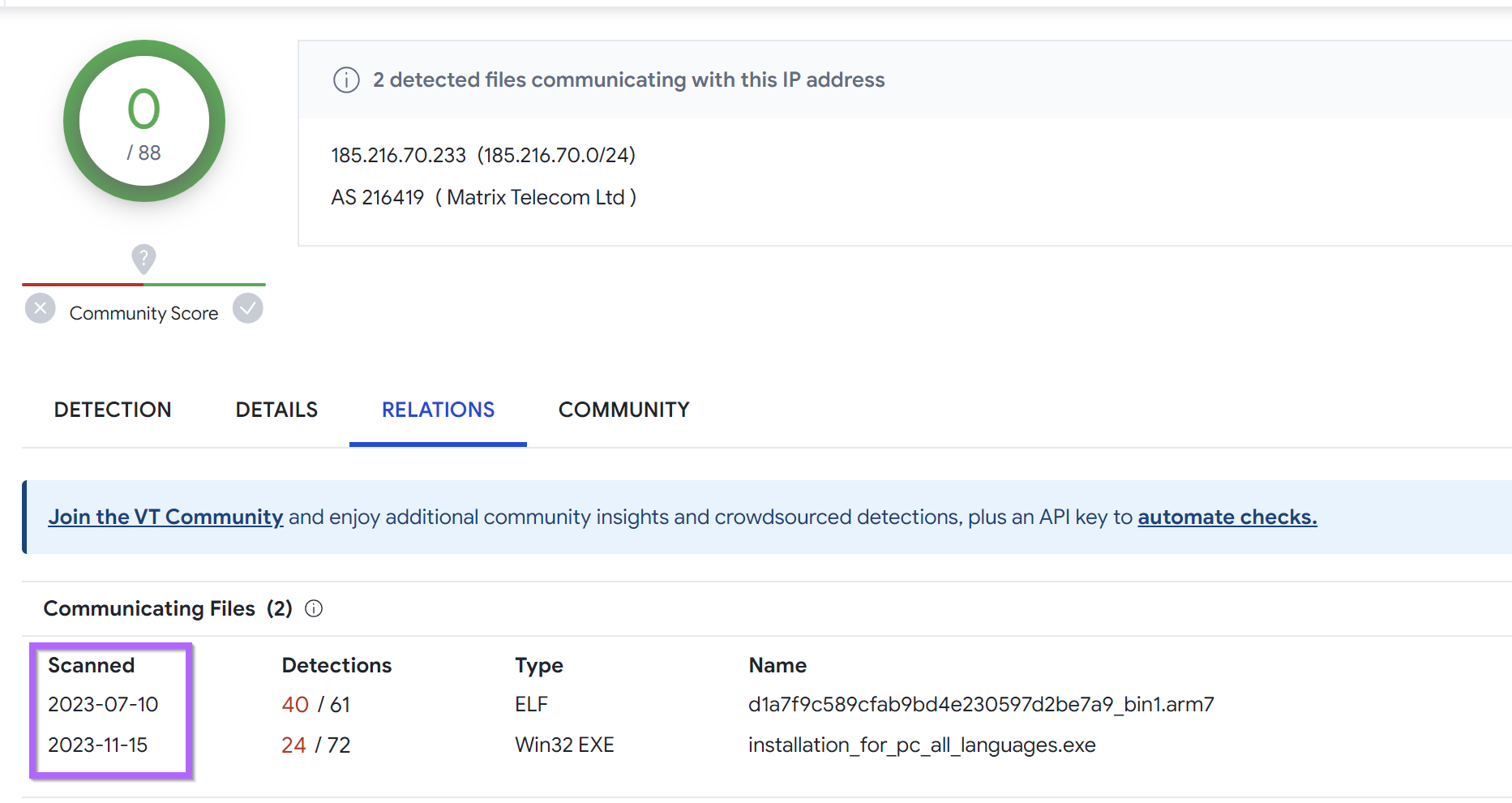
Another server 185.216.70[.]233 has 0/88 detections, with malicious files communicating as far back as July 2023.
The rest of the servers were largely repeats of those already mentioned. A full list of the results can be found below.
List of Returned C2's
#RisePro Server List - VT Detections as of 2023/11/15
5.42.92[.]51 - 12/88
37.27.22[.]139 - 2/88
45.15.156[.]137 - 1/88
85.209.11[.]247 - 7/88
91.103.253[.]146 - 1/88
109.107.182[.]9 - 1/88
128.140.73[.]191 - 0/88
152.89.198[.]49 - 1/88
185.216.70[.]222 - 1/88
185.216.70[.]233 - 0/88
185.216.70[.]238 - 13/88
194.49.94[.]41 - 1/88
194.169.175[.]113 - 1/88
194.169.175[.]122 - 1/88
194.169.175[.]123 - 1/88
194.169.175[.]128 - 20/88Sign up for Embee Research
Malware Analysis Tutorials
No spam. Unsubscribe anytime.
