In this post we leverage passive DNS analysis tools to expand on an ACTINIUM intelligence report published by Microsoft.
This analysis will leverage the initial domains provided in the report to identify new domains of interest that match the reported style and structure detailed in the original report. The initial report was published in 2022, so the idea here is to simply expand and update on the initial intelligence.
The TLDR of this analysis is that we will leverage passive DNS analysis to identify common patterns (IP, Registration dates, Subdomain Patterns) in the domains provided by Microsoft, we will then leverage this pattern to obtain updated ACTINIUM domains which were not included (or likely have been added after) the publication of the initial report.
It is worth noting that the initial report from Microsoft is nearly 2 years old. The "new" intelligence obtained here simply highlights changes to the ACTINIUM infrastructure since the initial report was published. The initial report is fantastic and Microsoft almost certainly knows everything published here.
The key point of this blog is to highlight technical methods that can be utilised to obtain the same intelligence with tooling that is accessible to regular analysts.
Initial Intelligence and IOC's
The initial intelligence and IOC's are taken from this Microsoft blog on the ACTINIUM threat actor.
Here, Microsoft shared a total of 124 domains related to the actor. We will be leveraging these domains to identify patterns and identify new infrastructure.
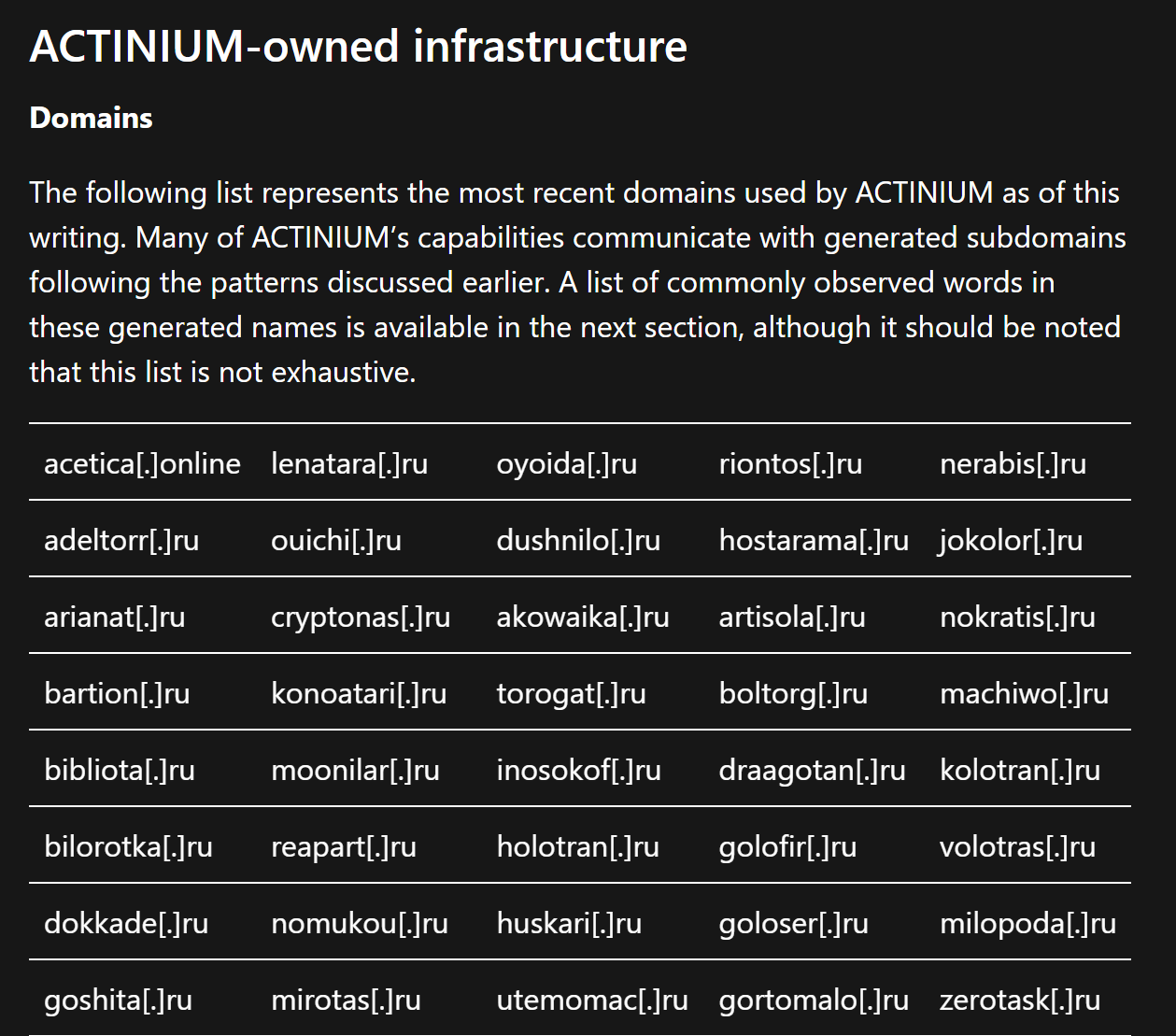
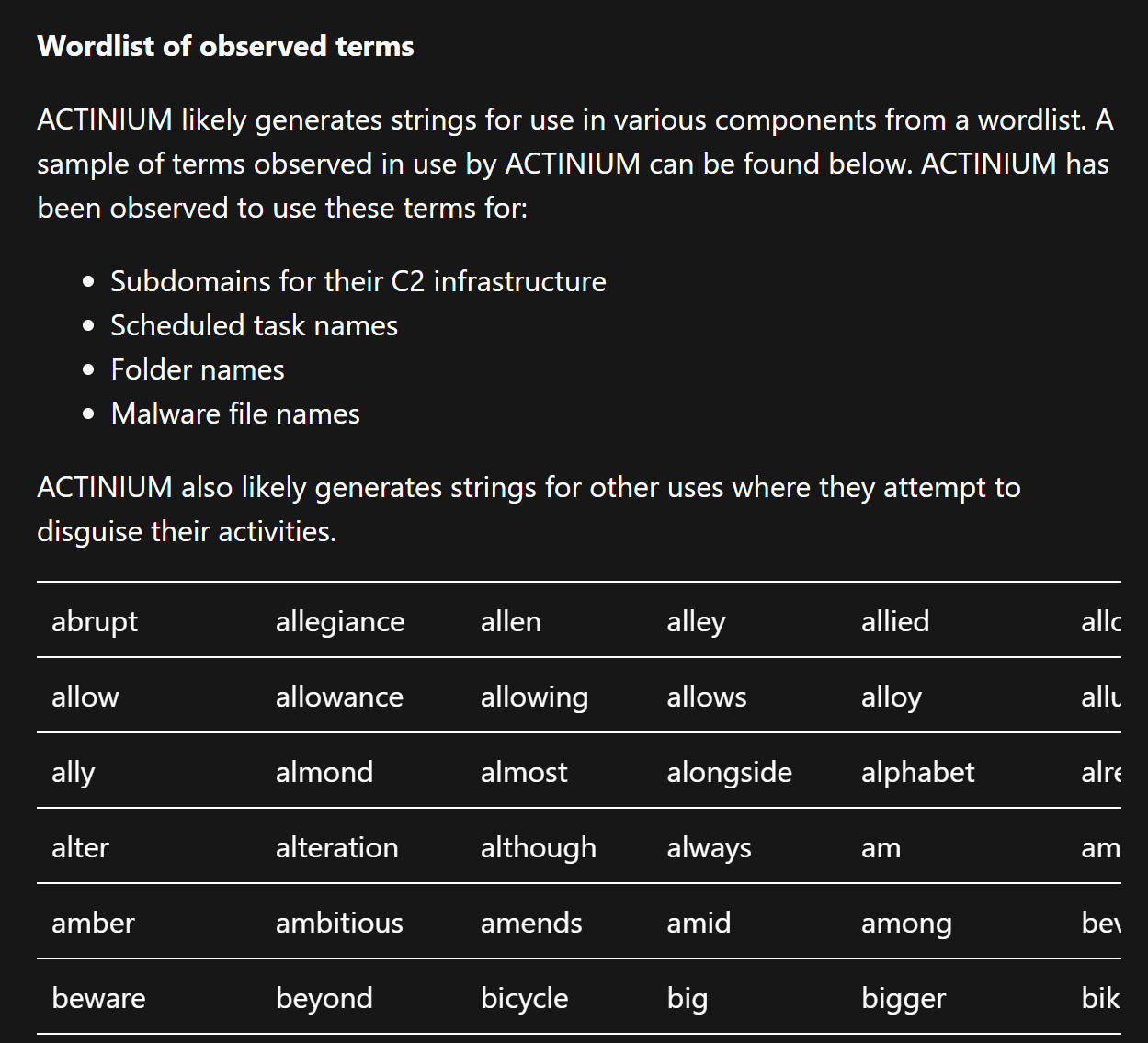
Microsoft has also reported that each of these domains has numerous subdomains which are generated from a wordlist.
The subdomain wordings are relatively random, and we will use this as an indicator to identify new domains.
Initial Search for IOC Commonalities
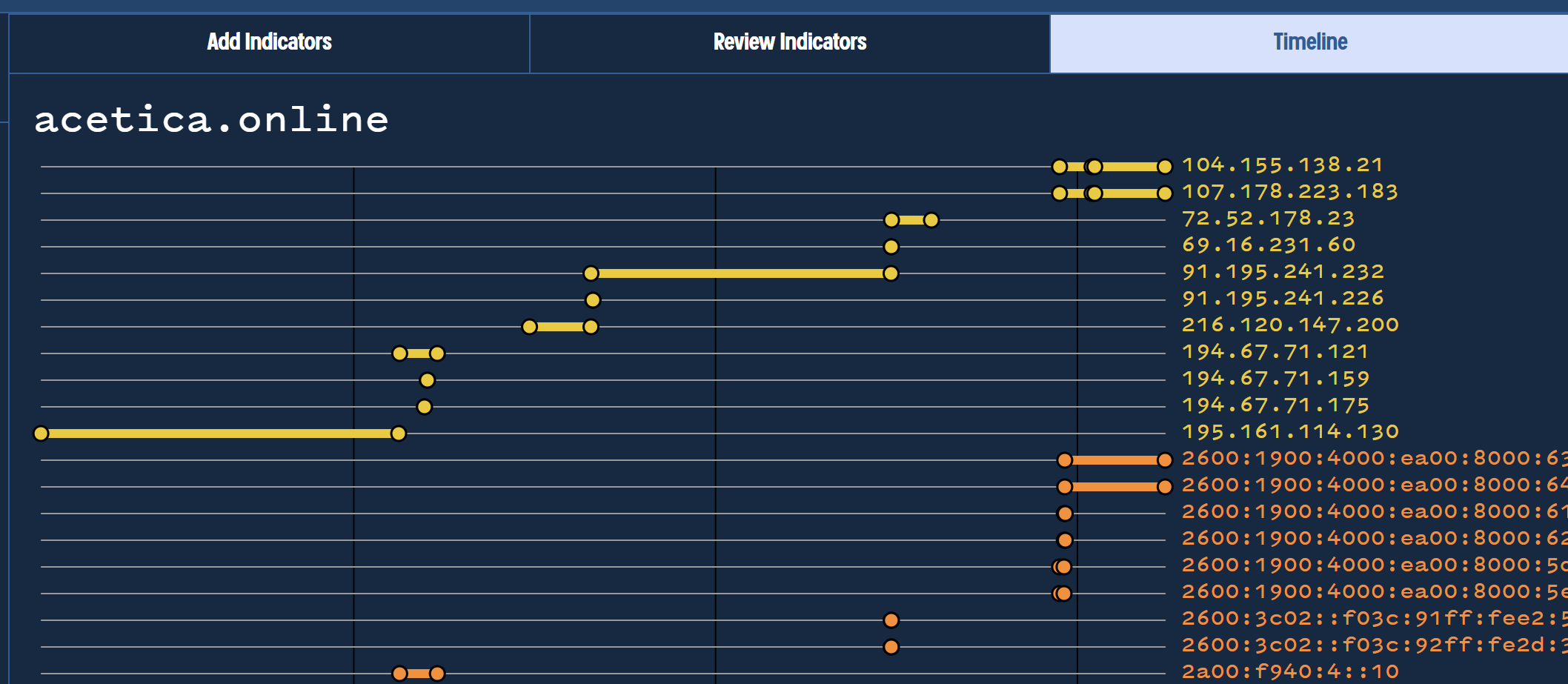
We can begin our analysis by performing a bulk search on the domains provided by Microsoft. We utilised Validin for this and a link to the bulk search can be found here.
This enables us to view the timelines of IP addresses utilised by the 124 domains reported by Microsoft.
The full results on the page are extremely as each domains has individually resolved to dozens of IP addresses over the last few years. (Hence it is difficult to screenshot the vast amount of information provided in the bulk search)
Here we can see a short snippet of the IP history for acetica[.]online from the Microsoft report.
We can also see the same for akowaika[.]ru
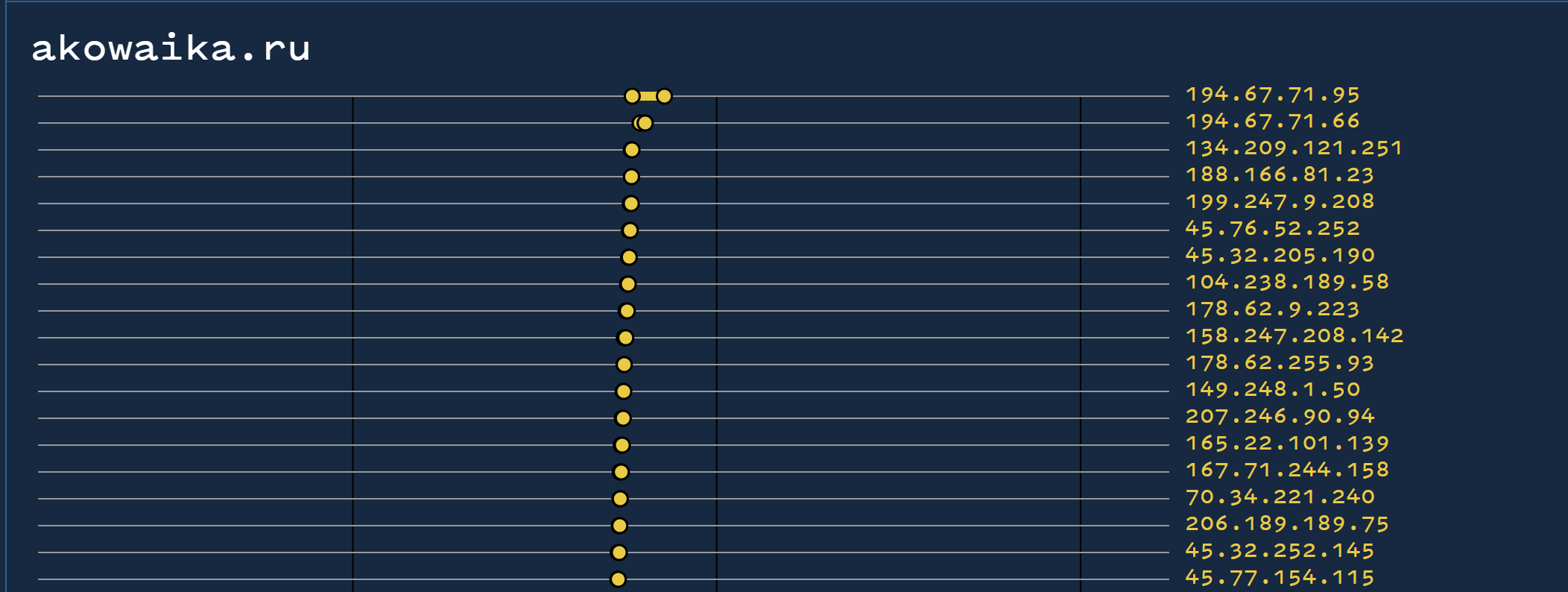
The bulk search results were huge (~20K indicators), so I exported the complete list and utilised CyberChef to sort the results.
Identifying Commonalities Using CyberChef
After exporting the results from Validin, we can import them into CyberChef and perform some basic analysis and sorting.
When accounting for all resolved records of the 124 initial domains, this export produced 20402 indicators (inclusive of duplicates where multiple domains shared the same IP).
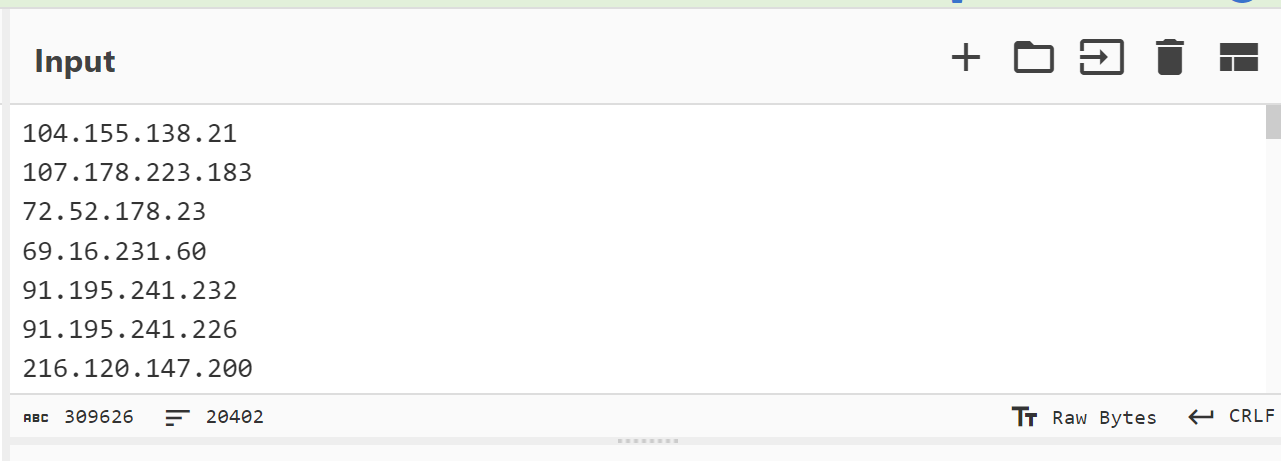
To better understand the data and identify pivot points, we can duplicate the results and use CyberChef to sort them by most occurrences.
The goal here is to identify infrastructure that was most re-used across the reported domains, and to use these as pivot points to identify new or unreported domains.
The sorting can be achieved with a Unique and Sort operation, which reveals the most common resolved IP address was 139.180.174[.]234, with 49 occurrences across the 124 initial domains.
Pivoting On The Resolved IP
We can take this most common IP 139.180.174[.]234 and search for it in the bulk export.
The goal here is to look for other patterns we can leverage.
In this case, we can see that the majority of IPs (not all shown here) were leveraging this IP only on 2022-07-27
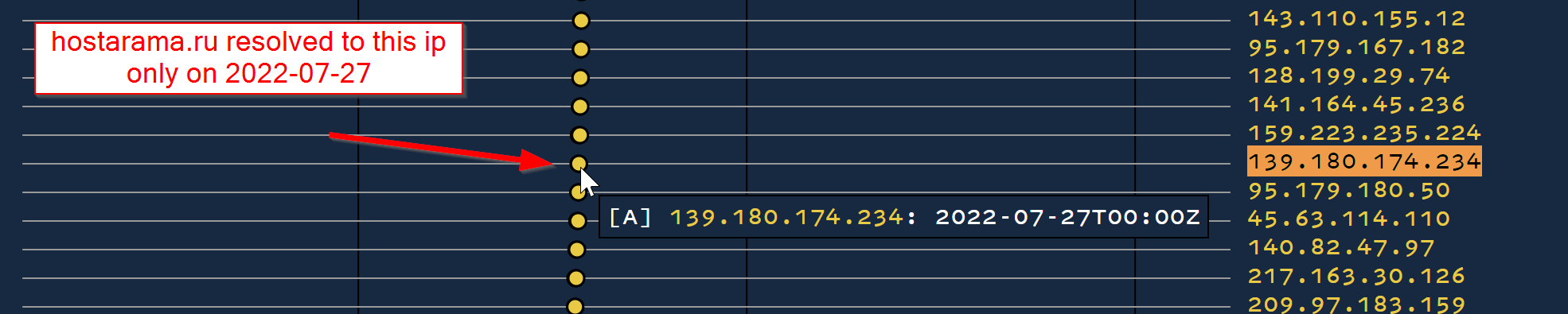
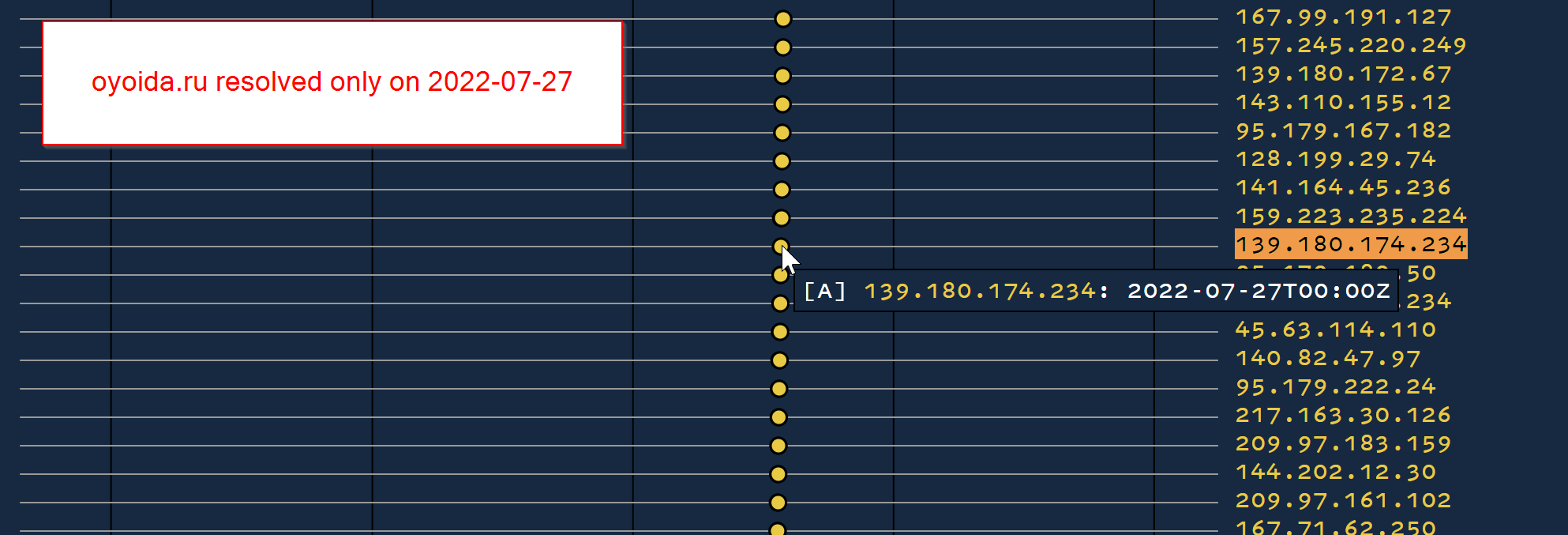
Pivoting On Usage Dates
Using this new information on the resolution dates, we can pivot on the IP address and specify that we only want DNS resolutions that first appeared around 2022-07-27.
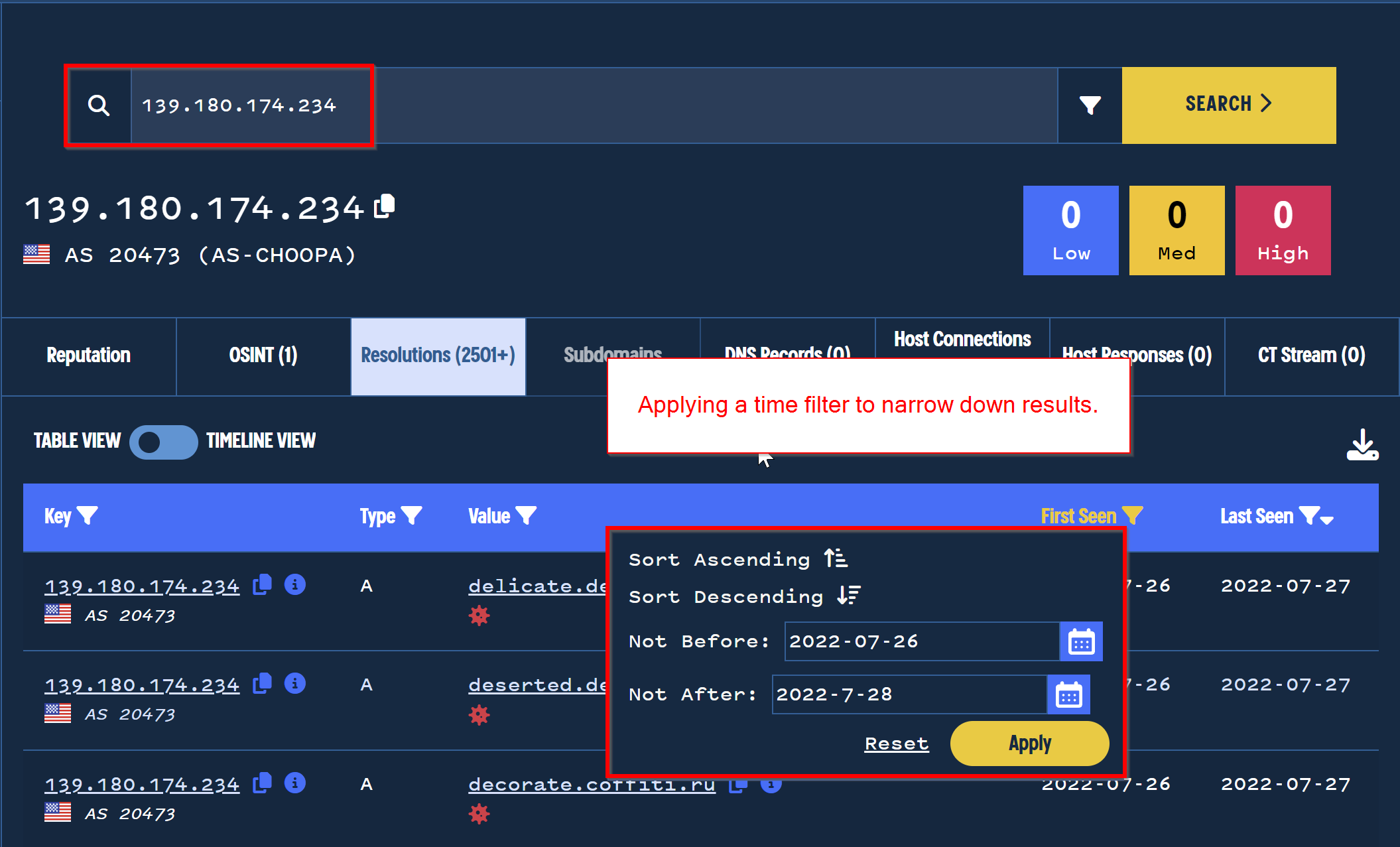
We can also apply a filter for .ru domains, in addition to the time filtering.
This immediately has some interesting results.
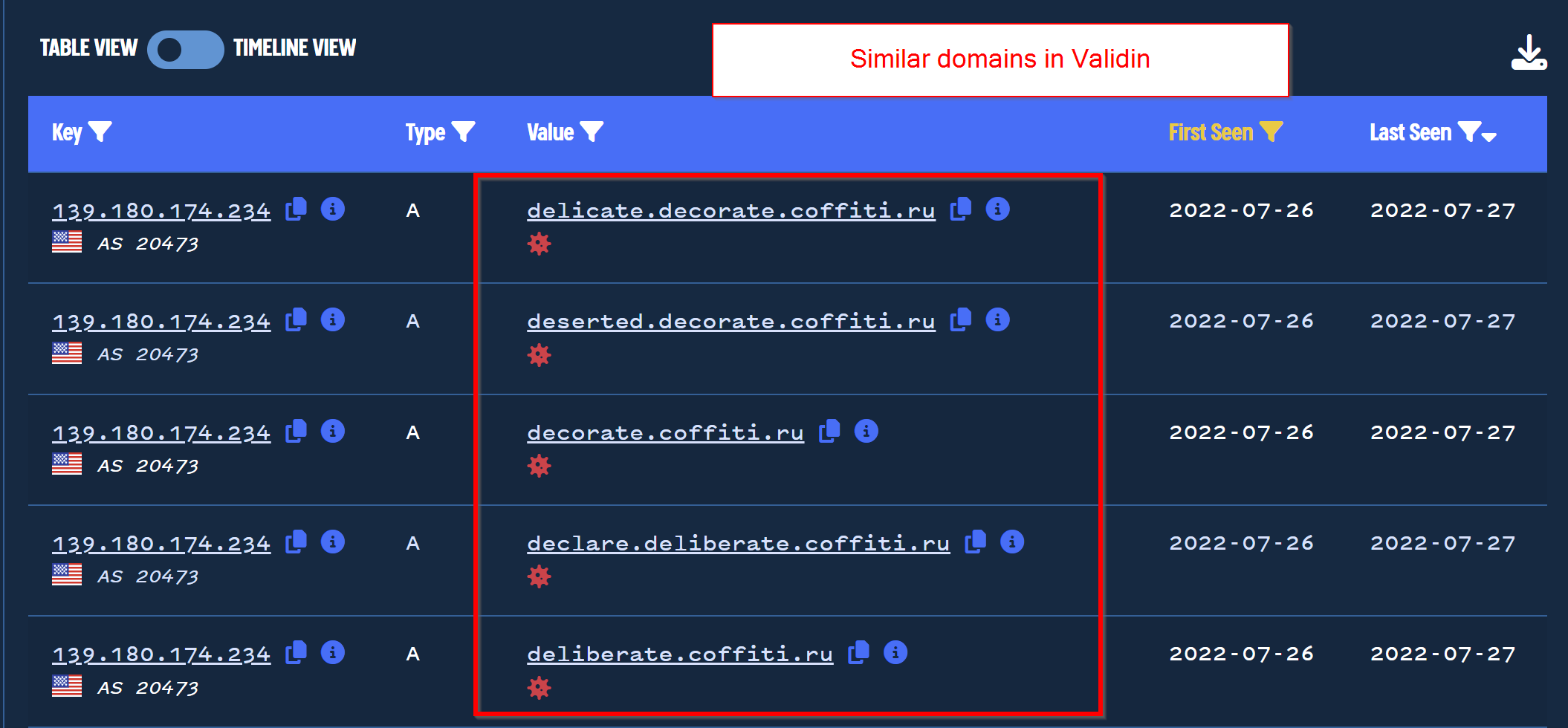
We can see that these initial results match the same subdomain style as reported by Microsoft.
After applying the time filters and .ru filter, Validin returns 2492 matching domains, including the various subdomains for each domain parent.
After exporting the search results, we can again see the same subdomain patterns.
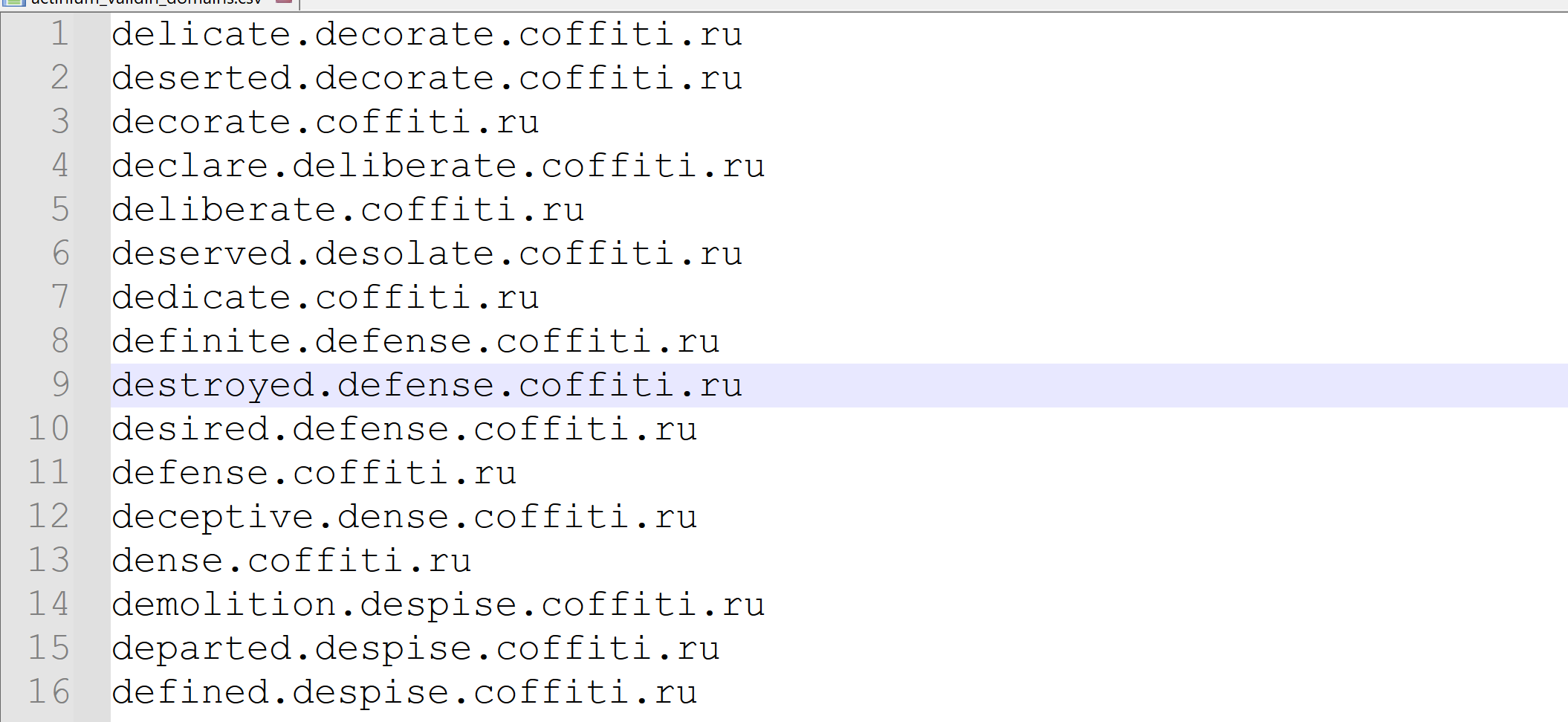
At this point, we wanted to extract only the primary domains like coffiti[.]ru, we didn't see a lot of value in keeping the entire list of subdomains.
To achieve this, we moved the export into CyberChef and applied a regular expression to extract the primary domains and sort them by the number of subdomains present.
For each domain in the below screenshot, the numerical value represents the number of subdomains observed.
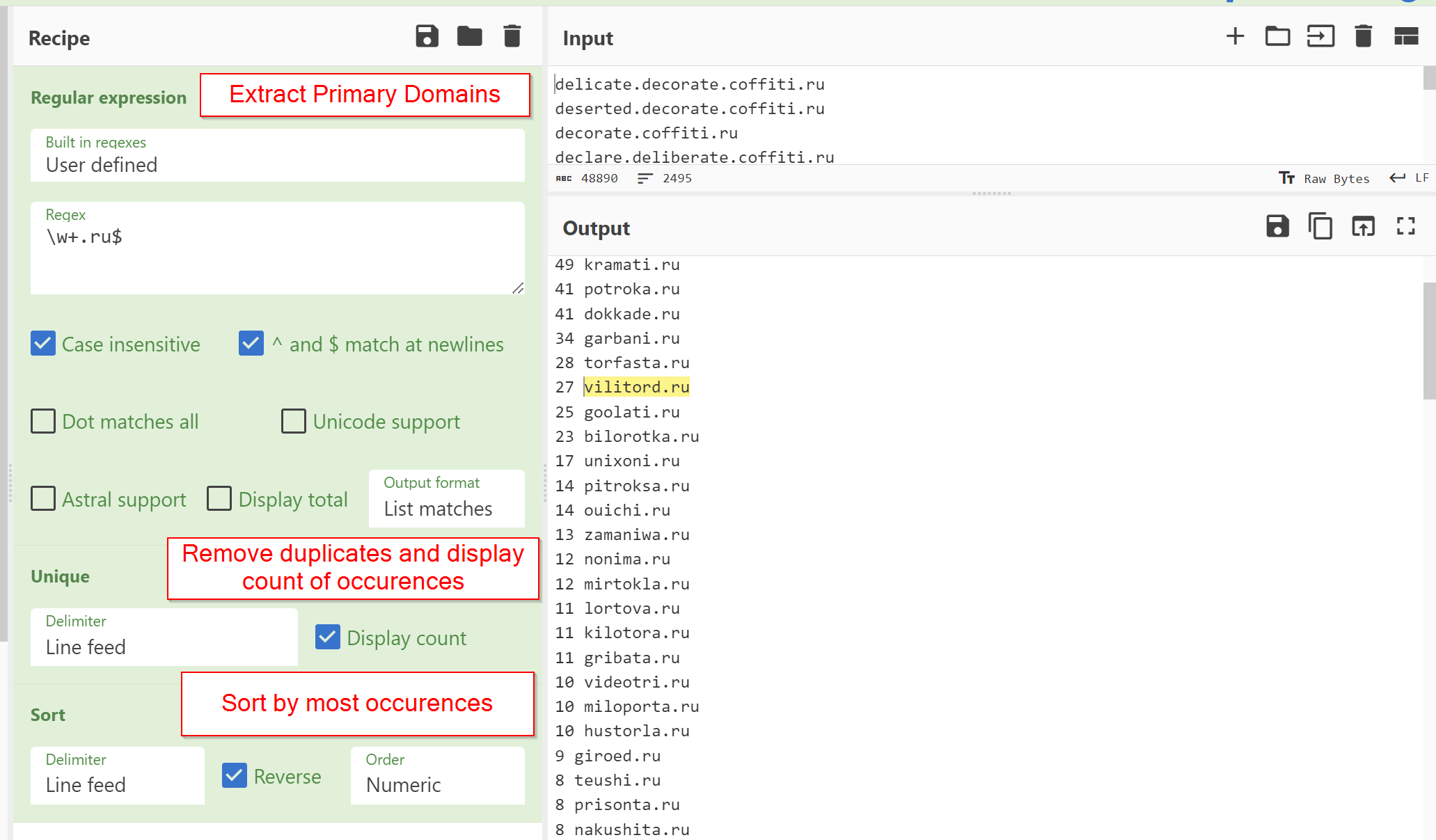
It was interesting to note that some of these domains were absent in the initial Microsoft report, indicating that we may have identified some new domains.
Comparison With Microsoft Report
We can now compare additional results with those from the Microsoft report.
Here is an example of the subdomains of bilorotka[.]ru, this domain WAS specified in the Microsoft report.
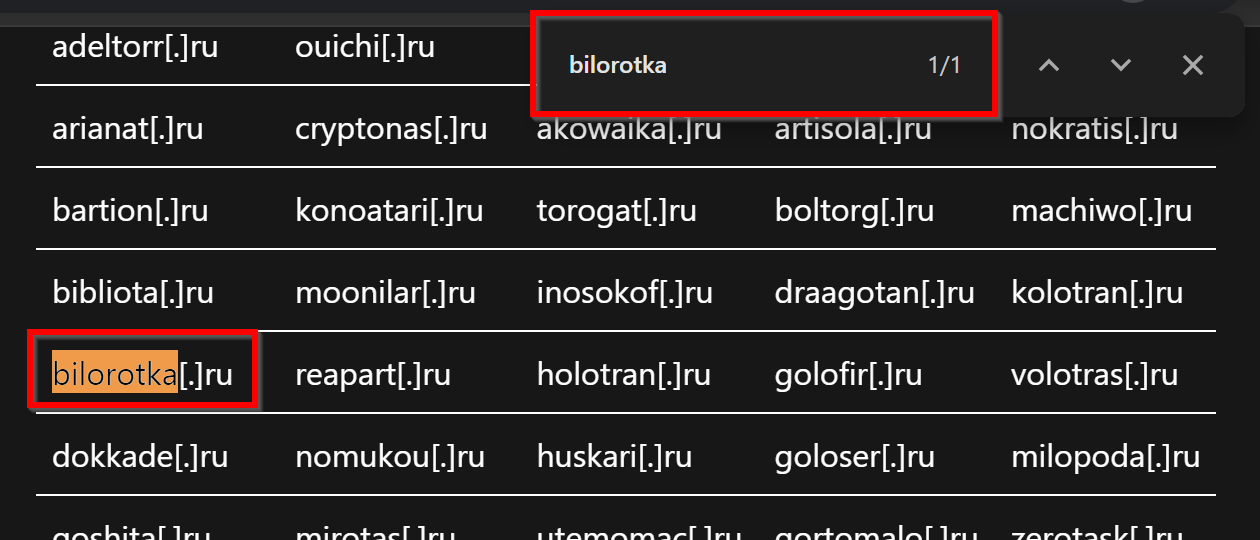
Here we can see that bilorotka[.]ru contains multiple subdomains with random wording.
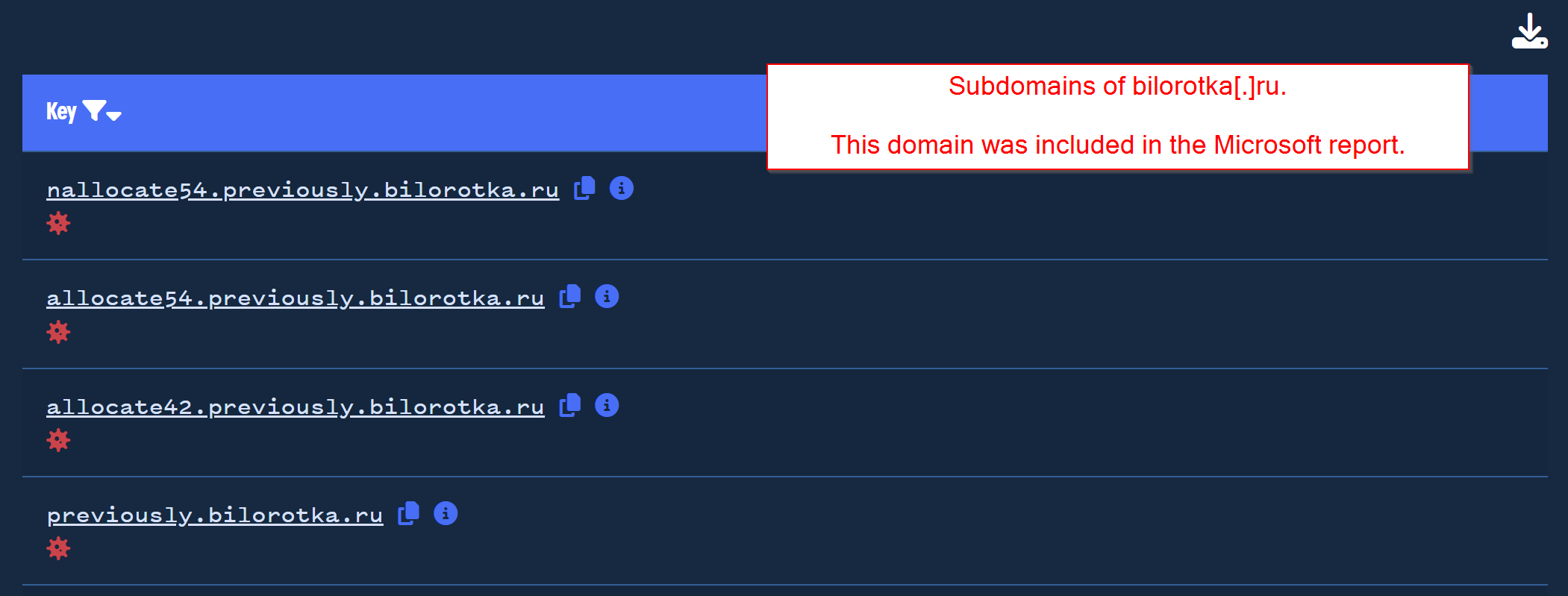
Now we can compare this to a domain from our Validin export enriched with CyberChef.
The domain torfasta[.]ru was not included in the initial report, and our results from Validin show that it matches a similar subdomain structure.
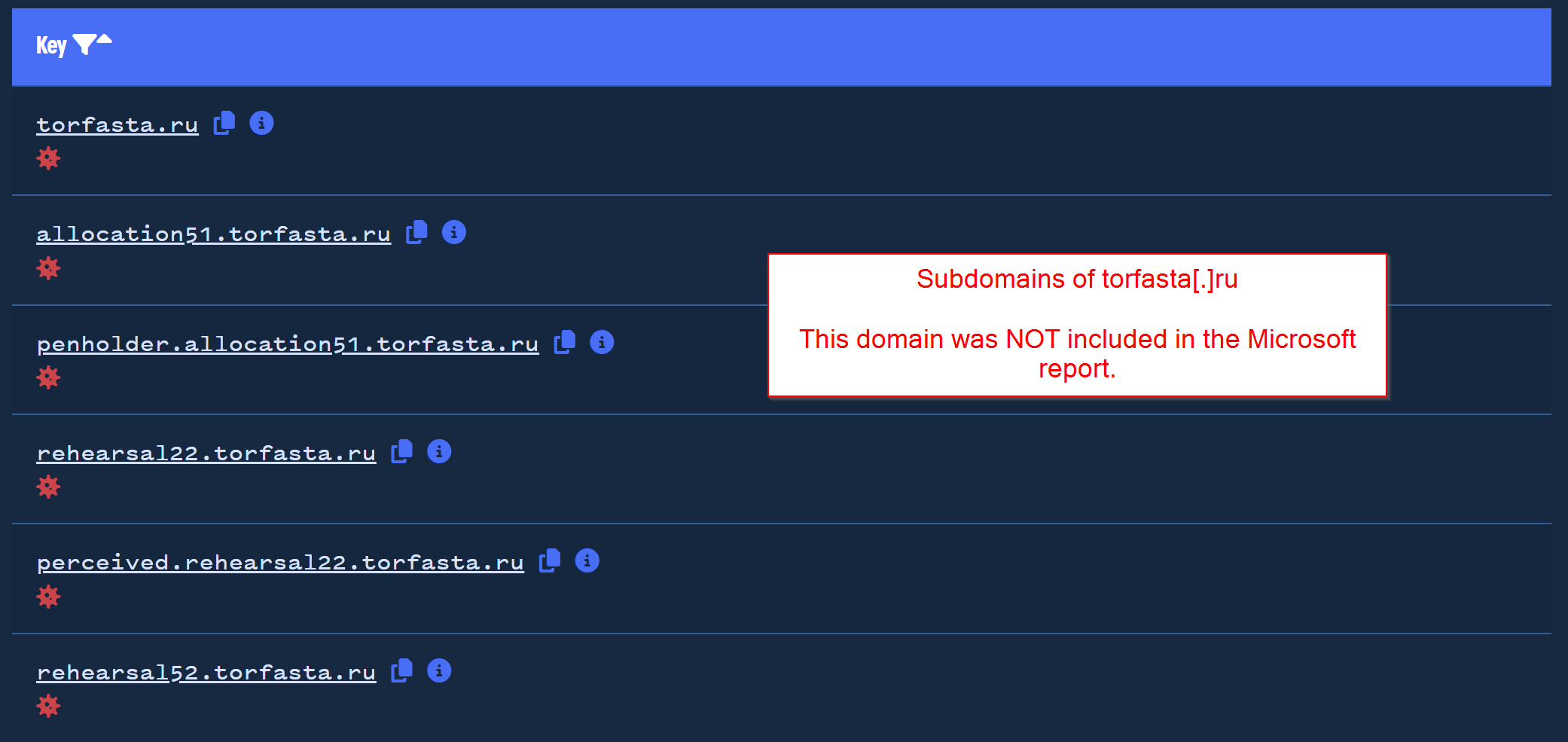
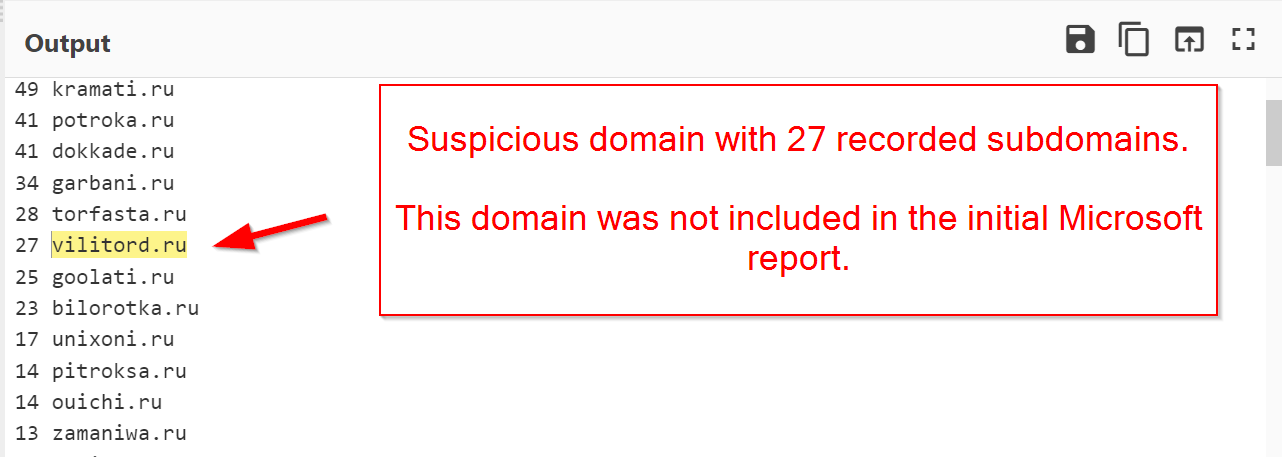
Performing the same search in Validin for vilitord[.]ru, we can see another slightly different but still very similar subdomain structure.
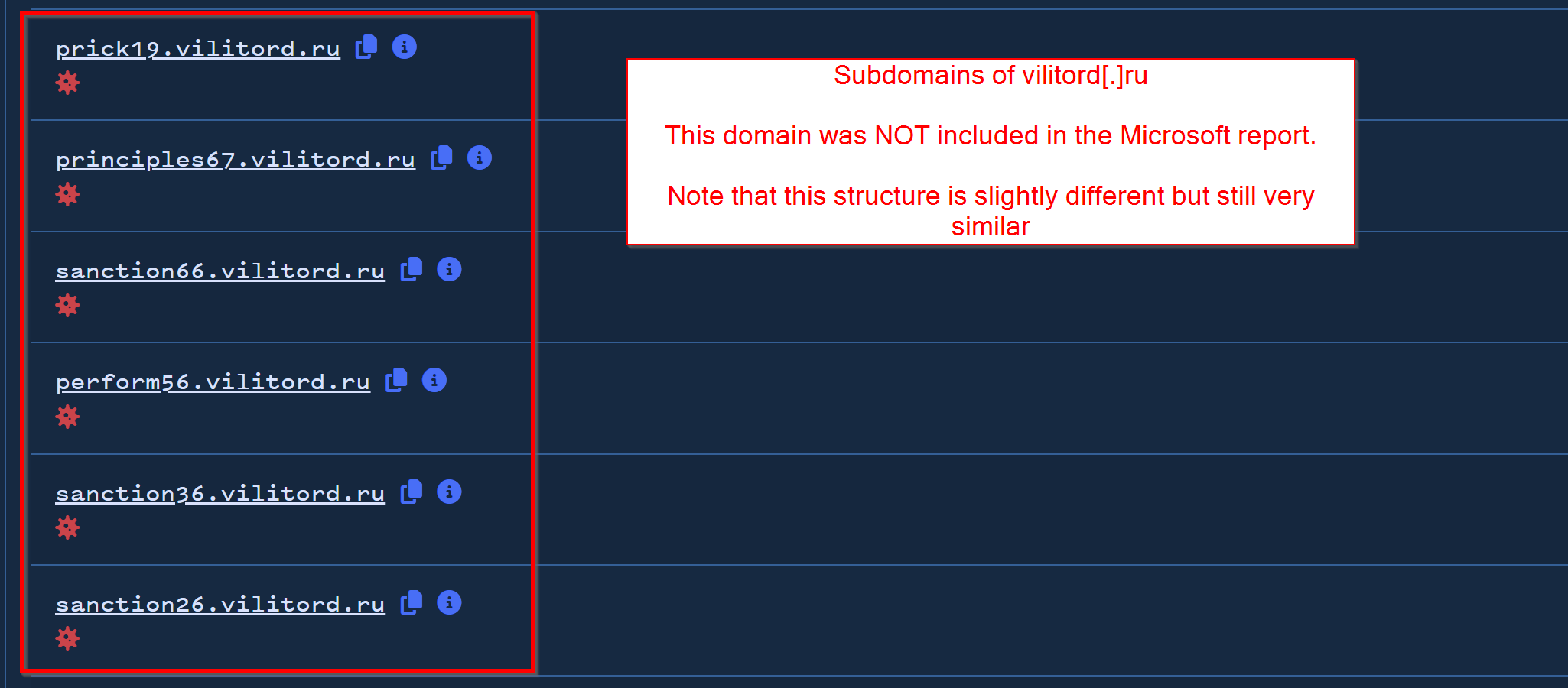
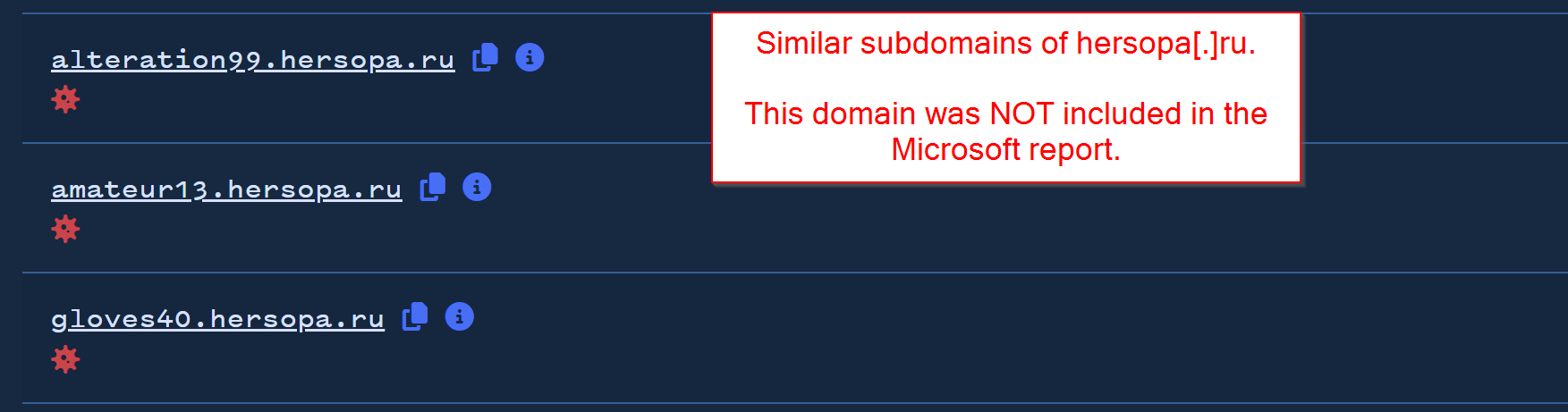
Expanding on another domain hersopa[.]ru (also not in the initial Microsoft report), we can identify another similar pattern. (Link to search here)
Comparing the Results and Identifying New Domains
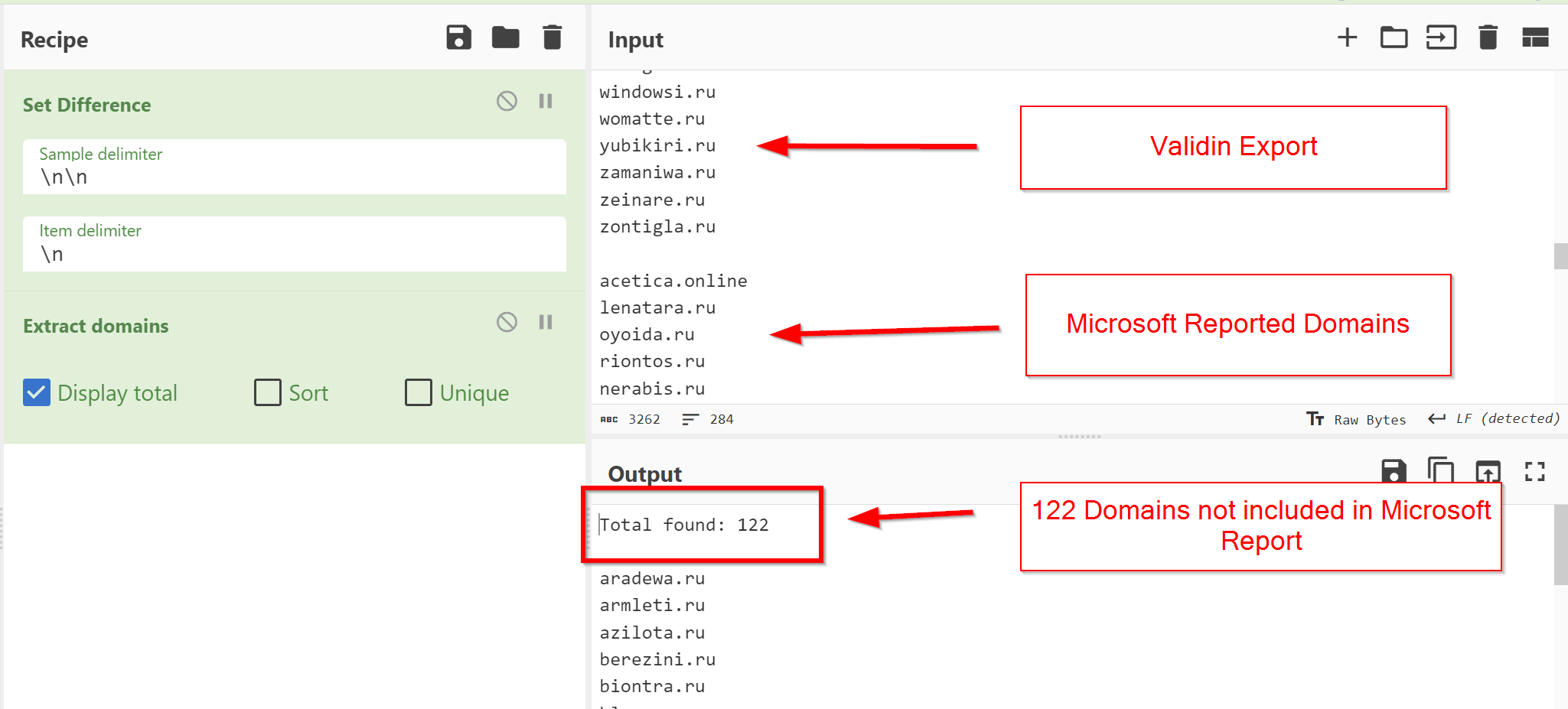
The results of our Validin export produced 159 unique .ru domains.
We decided to run a Set Difference with the Validin export vs the original Microsoft report.
Our results indicate that we may have identified an additional 122 domains.
It is possible that some of these are false positives, but the majority included very similar subdomains and were not included in the initial report.
Checking the results again in Validin, the subdomains are again consistent with that of the initial reporting and known malicious domains.
This pattern was consistent across the ~30 domains we checked from the Set Difference obtained in CyberChef. (It is possible that some did not match this structure)
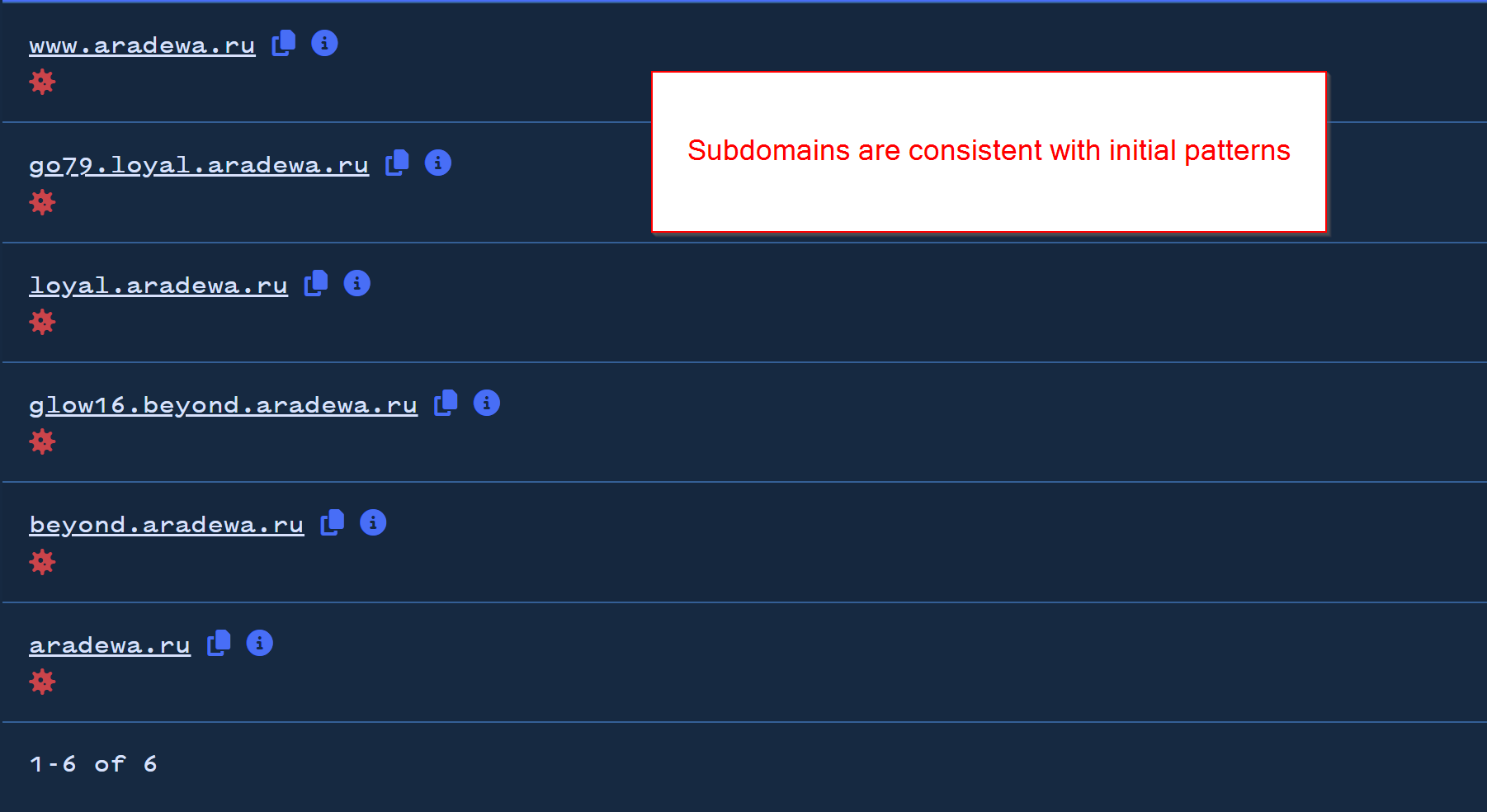
We were happy to conclude that the results were likely related to the same Threat Actor (given the same IP, registration dates and Subdomain patterns).
We did not validate every result, so it is possible that a small number were unrelated.
At this point, this process could be repeated for the other most popular IPs detailed in previous sections; we believe this would identify a significant amount more infrastructure.
In this analysis, we used only the most common IP, which was only present in 49/124 domains from the Microsoft report.

Conclusion
We have potentially identified an additional 122 domains linked to the same actor. We have achieved this using tooling (Validin, CyberChef) and intelligence (Microsoft Reports) that is easily available to anyone.
We wanted to publish this not as an intelligence report (The initial report was 2 years old and Microsoft almost certainly knows everything published here), but instead our goal was to make an educational guide on how others can do the same with free and low-cost tooling.
If you would like to recreate this analysis for yourself, we highly recommend checking out the community (free) edition of Validin and our previous analysis on passive DNS use cases.

Worthy Notes
- We confirmed many (but not all) of the final results matched the initial subdomain structure, some may be false positives.
- We did not do any validation beyond looking for the same subdomain structure, IP and Registration dates.
- The IP we used for pivoting was only common on 49/124 reported Microsoft domains; repeating this process for other IP pivots will likely obtain many more.
- There are domains reported by Microsoft that were not found in our results; this was likely because we only checked a single IP address.
Sign up for Embee Research
Malware Analysis and Threat Intelligence
No spam. Unsubscribe anytime.
Newly Identified Domains
amaniwa[.]ru
aradewa[.]ru
armleti[.]ru
asdorta[.]ru
azilota[.]ru
berezini[.]ru
biontra[.]ru
bluera[.]ru
bokujanai[.]ru
boltorg[.]ru
centosi[.]ru
cheesitra[.]ru
coffiti[.]ru
colibrita[.]ru
colopiri[.]ru
dirdiga[.]ru
donera[.]ru
erostipa[.]ru
filorta[.]ru
firatoska[.]ru
fukakumog[.]ru
garbani[.]ru
genkai[.]ru
giltorad[.]ru
giroed[.]ru
gloritapa[.]ru
golorta[.]ru
goolati[.]ru
gortova[.]ru
gribata[.]ru
guirora[.]ru
hersopa[.]ru
hikorta[.]ru
hilorra[.]ru
hilotrapa[.]ru
hirube[.]ru
historusi[.]ru
historyna[.]ru
hitrovana[.]ru
holorta[.]ru
holpantra[.]ru
holposta[.]ru
hostarama[.]ru
huskari[.]ru
hustorla[.]ru
hustorta[.]ru
idaite[.]ru
ienaike[.]ru
inosokof[.]ru
ishinde[.]ru
itsuke[.]ru
jistarka[.]ru
jittome[.]ru
jokrista[.]ru
jortiska[.]ru
kiesoud[.]ru
kilorta[.]ru
kilotora[.]ru
kilotra[.]ru
kilotrofa[.]ru
kimiga[.]ru
kimige[.]ru
kitta[.]ru
koete[.]ru
kolotara[.]ru
konoatari[.]ru
konokini[.]ru
koporta[.]ru
koraseba[.]ru
kotorapsa[.]ru
koutora[.]ru
kozikra[.]ru
kramati[.]ru
lenatara[.]ru
lestori[.]ru
lortova[.]ru
lotorda[.]ru
lotrosita[.]ru
lvihotra[.]ru
machic[.]ru
macosi[.]ru
martusi[.]ru
metronoc[.]ru
miharashi[.]ru
milopoda[.]ru
miloporta[.]ru
milotorpa[.]ru
mirtokla[.]ru
mirtopa[.]ru
mitlubald[.]ru
miwosaga[.]ru
molodora[.]ru
molortasa[.]ru
motorada[.]ru
muhicha[.]ru
mujakini[.]ru
nakona[.]ru
nijinda[.]ru
ninobotte[.]ru
nintara[.]ru
nodoka[.]ru
nostikarta[.]ru
ouichi[.]ru
oyoida[.]ru
pitroksa[.]ru
plortac[.]ru
potrahid[.]ru
potroka[.]ru
potrosiha[.]ru
potroska[.]ru
prisonta[.]ru
raidata[.]ru
rategade[.]ru
rawaumi[.]ru
ringali[.]ru
sadotra[.]ru
saihate[.]ru
samayoi[.]ru
satiri[.]ru
seitoshi[.]ru
selotra[.]ru
shopusi[.]ru
sisoshi[.]ru
soredake[.]ru
suzuite[.]ru
taraii[.]ru
teasagaki[.]ru
teushi[.]ru
titolora[.]ru
torfasta[.]ru
torohota[.]ru
tsuzuketa[.]ru
unixoni[.]ru
utemomac[.]ru
verusa[.]ru
videotri[.]ru
vilitord[.]ru
vitorog[.]ru
vodagi[.]ru
windowsi[.]ru
womatte[.]ru
yubikiri[.]ru
zamaniwa[.]ru
zeinare[.]ru
zontigla[.]ru