Dnspy
Reverse Engineering
|
Nov 01, 2023
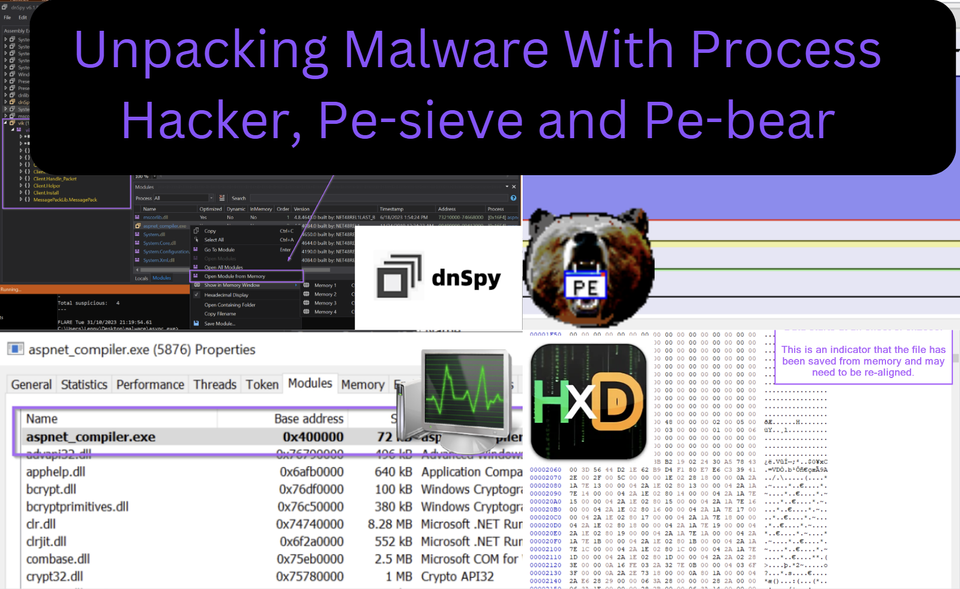
Demonstrating three additional methods for obtaining unpacked malware samples. Using Process Hacker, Pe-sieve, Hxd and Pe-bear.
Detection Engineering
|
Oct 10, 2023

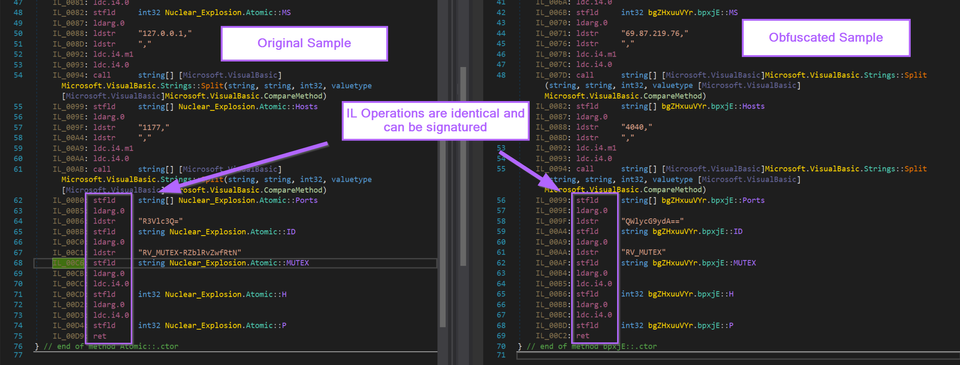
How to develop Yara rules for .NET Malware. Utilising IL instructions and associated bytecodes.
Threat Intelligence
|
May 15, 2023

Extraction of Quasar C2 configuration via Dnspy, and using this information to pivot to additional servers utilising Shodan and Censys.
Debugger Tutorials
|
May 07, 2023

Analysis of a Multi-Stage Loader for AgentTesla. Covering Ghidra, Dnspy, X32dbg, API Hashing and more!